Difference between revisions of "The Defenders: Proposal Version 1"
Jump to navigation
Jump to search
| Line 1: | Line 1: | ||
| + | |||
{| style="background-color:white; color:white padding: 5px 0 0 0;" width="100%" height=50px cellspacing="0" cellpadding="0" valign="top" border="0" | | {| style="background-color:white; color:white padding: 5px 0 0 0;" width="100%" height=50px cellspacing="0" cellpadding="0" valign="top" border="0" | | ||
| Line 105: | Line 106: | ||
<br> | <br> | ||
<div style="background: #FFFFFF; margin-top: 40px; font-weight: bold; line-height: 0.3em;letter-spacing:-0.08em;font-size:20px"><font color="#FF6347" face="Helvetica">KEY TECHNICAL CHALLENGES</font></div> | <div style="background: #FFFFFF; margin-top: 40px; font-weight: bold; line-height: 0.3em;letter-spacing:-0.08em;font-size:20px"><font color="#FF6347" face="Helvetica">KEY TECHNICAL CHALLENGES</font></div> | ||
| − | + | <br> | |
| − | + | [[File:TechChallenges.png|center|625px]] | |
| + | <br> | ||
<div style="background: #FFFFFF; margin-bottom:10px; margin-top: 40px; font-weight: bold; line-height: 0.3em;letter-spacing:-0.08em;font-size:20px"><font color=#FF7F50 face="Helvetica">PROJECT TIMELINE</font></div> | <div style="background: #FFFFFF; margin-bottom:10px; margin-top: 40px; font-weight: bold; line-height: 0.3em;letter-spacing:-0.08em;font-size:20px"><font color=#FF7F50 face="Helvetica">PROJECT TIMELINE</font></div> | ||
| − | + | <br> | |
| − | + | [[File:Timeline.png|center|600px]] | |
| + | <br> | ||
<div style="background: #FFFFFF; margin-top: 40px; font-weight: bold; line-height: 0.3em;letter-spacing:-0.08em;font-size:20px"><font color=#FF6347 face="Helvetica">REFERENCES</font></div> | <div style="background: #FFFFFF; margin-top: 40px; font-weight: bold; line-height: 0.3em;letter-spacing:-0.08em;font-size:20px"><font color=#FF6347 face="Helvetica">REFERENCES</font></div> | ||
Revision as of 02:01, 12 October 2018
SELECTED DATASET
| Breach Level Index | Header text |
|---|---|
| Source : Gemalto, the world leader in digital security. | Example |
| Purpose : Dataset is designed to provide a simple way to input publicly disclosed information on data breaches and calculate a score indicating breach severity. (https://breachlevelindex.com/) | Example |
|
1. Organization Breached 2. Number of Records Breached 3. Date of Breach: 01/01/2013 - 29/06/2018 4. Type of Breach -Nuisance (Email, Addresses, Affiliation) -Account Access (Username, Passwords to websites/ social media) -Financial Access (Bank Account Credentials) -Identity Theft ( Information can be used to masquerade someone) -Existential Data ( Info can be used to threaten business survival) 5. Source of Breach: -Lost Device -Stolen Device -Malicious Insider -Malicious Outsider -State Espionage 6. Location: Country 7. Industry: -Technology, Other, Retail, Government, Healthcare, Education -Financial, Social Media, Hospitality, Entertainment, Insurance -Non-profit, Industrial, Professional Services 8. Risk Score: Log 10 ( Type of Data * Source of Breach * Whether Action was taken) |
Example |
BACKGROUND SURVEY OF RELATED WORKS
| Related Works | What We Can Learn |
|---|---|
|
|
|
SKETCHES STORYBOARD
| Sketches | How Analyst Can Conduct Analysis |
|---|---|
|
|
|
|
|
ARCHITECTURE DIAGRAM
KEY TECHNICAL CHALLENGES
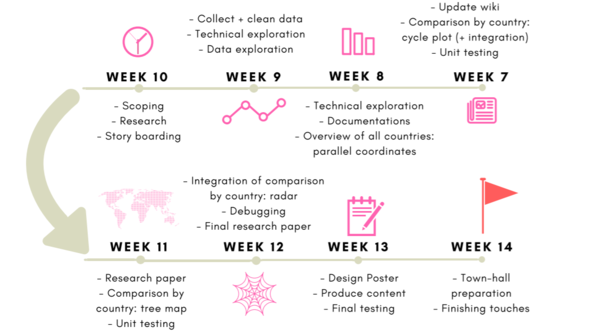
PROJECT TIMELINE
REFERENCES
COMMENTS
Feel free to comments, suggestions and feedbacks to help us improve our project!:D