Difference between revisions of "The Defenders: Proposal Version 1"
| Line 17: | Line 17: | ||
| − | <div style="background: #FFFFFF; margin-top: 40px; font-weight: bold; line-height: 0.3em;letter-spacing:-0.08em;font-size:20px"><font color=# | + | <div style="background: #FFFFFF; margin-top: 40px; font-weight: bold; line-height: 0.3em;letter-spacing:-0.08em;font-size:20px"><font color=#FF0090 face="Helvetica">SELECTED DATASET</font></div> |
| Line 106: | Line 106: | ||
</p> | </p> | ||
| − | <div style="background: #FFFFFF; margin-top: 40px; font-weight: bold; line-height: 0.3em;letter-spacing:-0.08em;font-size:20px"><font color=# | + | <div style="background: #FFFFFF; margin-top: 40px; font-weight: bold; line-height: 0.3em;letter-spacing:-0.08em;font-size:20px"><font color=#FF0090 face="Helvetica">BACKGROUND SURVEY OF RELATED WORKS</font></div> |
| Line 112: | Line 112: | ||
| − | <div style="background: #FFFFFF; margin-top: 40px; font-weight: bold; line-height: 0.3em;letter-spacing:-0.08em;font-size:20px"><font color="# | + | <div style="background: #FFFFFF; margin-top: 40px; font-weight: bold; line-height: 0.3em;letter-spacing:-0.08em;font-size:20px"><font color="#FF0090" face="Helvetica">SKETCHES STORYBOARD</font></div> |
{| class="wikitable" style="background-color:#FFFFFF;" width="100%" | {| class="wikitable" style="background-color:#FFFFFF;" width="100%" | ||
! style="width:50%" | Sketches | ! style="width:50%" | Sketches | ||
| Line 184: | Line 184: | ||
|- | |- | ||
|} | |} | ||
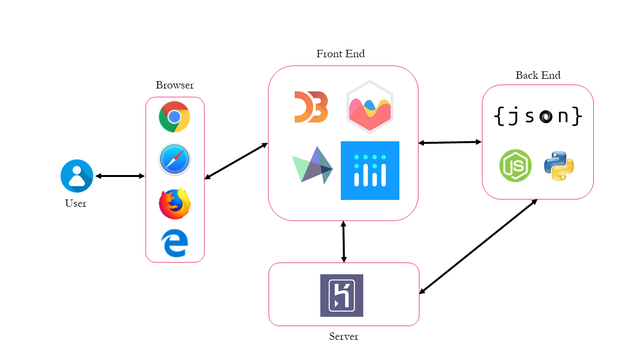
| − | <div style="background: #FFFFFF; margin-top: 40px; font-weight: bold; line-height: 0.3em;letter-spacing:-0.08em;font-size:20px"><font color="# | + | <div style="background: #FFFFFF; margin-top: 40px; font-weight: bold; line-height: 0.3em;letter-spacing:-0.08em;font-size:20px"><font color="#FF0090" face="Helvetica">ARCHITECTURE DIAGRAM</font> |
</div> | </div> | ||
| Line 190: | Line 190: | ||
[[File:Architecture Diagram.png|center|625px]] | [[File:Architecture Diagram.png|center|625px]] | ||
<br> | <br> | ||
| − | <div style="background: #FFFFFF; margin-top: 40px; font-weight: bold; line-height: 0.3em;letter-spacing:-0.08em;font-size:20px"><font color="# | + | <div style="background: #FFFFFF; margin-top: 40px; font-weight: bold; line-height: 0.3em;letter-spacing:-0.08em;font-size:20px"><font color="#FF0090" face="Helvetica">KEY TECHNICAL CHALLENGES</font></div> |
<br> | <br> | ||
[[File:TechChallenges.png|center|625px]] | [[File:TechChallenges.png|center|625px]] | ||
<br> | <br> | ||
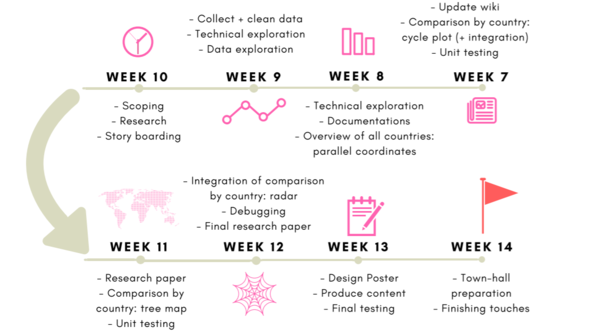
| − | <div style="background: #FFFFFF; margin-bottom:10px; margin-top: 40px; font-weight: bold; line-height: 0.3em;letter-spacing:-0.08em;font-size:20px"><font color=# | + | <div style="background: #FFFFFF; margin-bottom:10px; margin-top: 40px; font-weight: bold; line-height: 0.3em;letter-spacing:-0.08em;font-size:20px"><font color=#FF0090 face="Helvetica">PROJECT TIMELINE</font></div> |
<br> | <br> | ||
[[File:Timeline.png|center|600px]] | [[File:Timeline.png|center|600px]] | ||
<br> | <br> | ||
| − | <div style="background: #FFFFFF; margin-top: 40px; font-weight: bold; line-height: 0.3em;letter-spacing:-0.08em;font-size:20px"><font color=# | + | <div style="background: #FFFFFF; margin-top: 40px; font-weight: bold; line-height: 0.3em;letter-spacing:-0.08em;font-size:20px"><font color=#FF0090 face="Helvetica">REFERENCES</font></div> |
1. https://www.csa.gov.sg/news/press-releases/cyber-threats-in-singapore-grew-in-2017-mirroring-global-trends | 1. https://www.csa.gov.sg/news/press-releases/cyber-threats-in-singapore-grew-in-2017-mirroring-global-trends | ||
<br> | <br> | ||
| Line 220: | Line 220: | ||
<br><br> | <br><br> | ||
| − | <div style="background: #FFFFFF; margin-top: 40px; font-weight: bold; line-height: 0.3em;letter-spacing:-0.08em;font-size:20px"><font color=# | + | <div style="background: #FFFFFF; margin-top: 40px; font-weight: bold; line-height: 0.3em;letter-spacing:-0.08em;font-size:20px"><font color=#FF0090 face="Helvetica">COMMENTS</font></div> |
Feel free to comments, suggestions and feedbacks to help us improve our project!:D | Feel free to comments, suggestions and feedbacks to help us improve our project!:D | ||
Revision as of 17:42, 18 October 2018
| 1.Breach Level Index |
|---|
| Source : Gemalto, the world leader in digital security. |
| Purpose : Dataset is designed to provide a simple way to input publicly disclosed information on data breaches and calculate a score indicating breach severity. (https://breachlevelindex.com/) |
|
1. Organization Breached 2. Number of Records Breached 3. Date of Breach: 01/01/2013 - 29/06/2018 4. Type of Breach -Nuisance (Email, Addresses, Affiliation) -Account Access (Username, Passwords to websites/ social media) -Financial Access (Bank Account Credentials) -Identity Theft ( Information can be used to masquerade someone) -Existential Data ( Info can be used to threaten business survival) 5. Source of Breach: -Lost Device -Stolen Device -Malicious Insider -Malicious Outsider -State Espionage 6. Location: Country 7. Industry: -Technology, Other, Retail, Government, Healthcare, Education -Financial, Social Media, Hospitality, Entertainment, Insurance -Non-profit, Industrial, Professional Services 8. Risk Score: Log 10 ( Type of Data * Source of Breach * Whether Action was taken)
|
| 2. The world bank | 3. Percentage of Individual using the internet | 4. Human Development Reports |
|---|---|---|
| Source: The World Bank Group’s (WBG) Fragile, Conflict and Violence Group (formally the Center on Conflict, Security and Development CCSD) annually releases the Harmonized List of Fragile Situations. |
Source: World bank group |
Source: Barro-Lee Educational Attainment Dataset |
| Purpose: Stronger collaboration with humanitarian, development, peace and security partners is critical for delivery in challenging environments, such as in the Bank’s response to famine. |
Purpose: Overview of Internet Penetration to date (http://www.worldbank.org/) |
Purpose: Serves as a measure of achievement in the basic dimensions of human development across countries. (http://www.hdr.undp.org/en) |
|
1. Year 2. Conflict and Unrest |
1. Year 2. Individuals using the Internet (% of population) |
1. Literacy rate 2. Government expenditure on education (% of total expenditure) 3. Gross domestic product : Monetary measure of the market value of all the final goods and services produced in a period of time, often annually or quarterly. 4. Employment OR unemployment |
| Sketches | How Analyst Can Conduct Analysis |
|---|---|
|
|
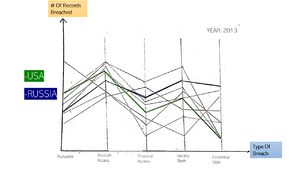
Breach OverviewConsists of an interactive parallel coordinate chart. This visualisation is linked by setting the time period for the data observed through an interactive timeframe. Parallel Coordinates The parallel coordinates show the distribution of each feature amongst the different countries. The use of brushing is to highlight the selected country/countries in relation to the rest of the countries. Dynamic Timeframe Toggle timeframe according to the period to be visualised. |
|
|
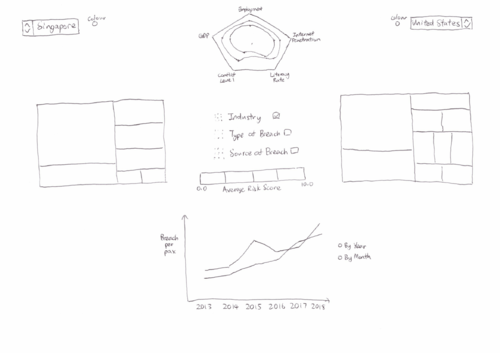
Risk ComparisonConsists of an interactive line chart, 2 treemaps and a radar chart. These visualisations are linked by checkboxes that detail various features such as type of industry, type of breach and source of breach. Both countries can be toggled and changed to other countries via a dropdown list. Line Chart The line chart compares the breaches per pax for 2 countries determined via the dropdown list. The corresponding colors of each country located beside the flag will match the color used for the lines in the line graph Toggle to display trend by year or by month in a cycle plot. Tooltip when hovering the mouse over to show information on:
Treemap The treemap shows a high level view of our breaches and displaying the breach details at the same time. The different rectangles in the treemap will be colored with different intensities based on risk scores. It allows us to see patterns quickly when our eyes visually aggregate rectangles in the same group. Checkbox to check the different features that we would like to drill down to. Toggle year to display different years’ results. Tooltip when hovering the mouse over to show:
Radar Chart The radar chart shows the breakdown of different Human Development Index indicators of various countries shown side by side. This allows us to see the possible different types of countries and see the relation these indicators may have with the breaches the country suffers from Toggle year to display different years’ results. Tooltip when hovering the mouse over to show the exact figure of the particular index. |
1. https://www.csa.gov.sg/news/press-releases/cyber-threats-in-singapore-grew-in-2017-mirroring-global-trends
2. https://www.todayonline.com/singapore/cyber-threats-singapore-go-phishing-attacks-see-biggest-jump
3. https://www.mcafee.com/enterprise/en-us/solutions/lp/economics-cybercrime.html
4. http://bl.ocks.org/mthh/7e17b680b35b83b49f1c22a3613bd89f
5. http://www.perceptualedge.com/articles/guests/intro_to_cycle_plots.pdf
Data Sources:
http://hdr.undp.org/en/data#
https://datacatalog.worldbank.org/dataset/harmonized-list-fragility-conflict-and-violence-countries
http://databank.worldbank.org/data/reports.aspx?source=2&series=IT.NET.USER.ZS#
Feel free to comments, suggestions and feedbacks to help us improve our project!:D