Difference between revisions of "The Defenders: Proposal Version 1"
| (22 intermediate revisions by 3 users not shown) | |||
| Line 1: | Line 1: | ||
| − | + | <span class="mw-ui-button {{#switch: {{{color|white}}} | red = mw-ui-destructive | green = mw-ui-constructive | white = | blue = mw-ui-progressive}}">[[Project_Groups|{{{Clickable Button|Back to Project Home}}}]]</span><noinclude> | |
| + | {| style="background-color:white; color:white padding: 5px 0 0 0;" width="100%" height=50px cellspacing="0" cellpadding="0" valign="top" border="0" | | ||
| − | | style="background:#ffe4b5;vertical-align:top;width:16%;" | <div style="padding: 3px; font-weight: bold; text-align:center; line-height: wrap_content; font-size:16px; solid #ffe4b5; background #ffe4b5; border-bottom:1px solid #ffe4b5; border-top:1px solid #ffe4b5; font-family:helvetica"> [[The Defenders: Proposal | + | | style="background:#ffe4b5;vertical-align:top;width:16%;" | <div style="padding: 3px; font-weight: bold; text-align:center; line-height: wrap_content; font-size:16px; solid #ffe4b5; background #ffe4b5; border-bottom:1px solid #ffe4b5; border-top:1px solid #ffe4b5; font-family:helvetica"> [[The Defenders: Proposal | <b>Proposal</b>]] |
| style="background:#ffe4b5;vertical-align:top;width:16%;" | <div style="padding: 3px; font-weight: bold; text-align:center; line-height: wrap_content; font-size:16px; solid #ffe4b5; background #ffe4b5; border-bottom:1px solid #ffe4b5; border-top:1px solid #ffe4b5; font-family:helvetica"> [[The Defenders: Poster | <b>Poster</b>]] | | style="background:#ffe4b5;vertical-align:top;width:16%;" | <div style="padding: 3px; font-weight: bold; text-align:center; line-height: wrap_content; font-size:16px; solid #ffe4b5; background #ffe4b5; border-bottom:1px solid #ffe4b5; border-top:1px solid #ffe4b5; font-family:helvetica"> [[The Defenders: Poster | <b>Poster</b>]] | ||
| Line 8: | Line 9: | ||
| style="background:#ffe4b5;vertical-align:top;width:16%;" | <div style="padding: 3px; font-weight: bold; text-align:center; line-height: wrap_content; font-size:16px; solid #ffe4b5; background #ffe4b5; border-bottom:1px solid #ffe4b5; border-top:1px solid #ffe4b5; font-family:helvetica"> [[The Defenders: Research Paper | <b>Research Paper</b>]] | | style="background:#ffe4b5;vertical-align:top;width:16%;" | <div style="padding: 3px; font-weight: bold; text-align:center; line-height: wrap_content; font-size:16px; solid #ffe4b5; background #ffe4b5; border-bottom:1px solid #ffe4b5; border-top:1px solid #ffe4b5; font-family:helvetica"> [[The Defenders: Research Paper | <b>Research Paper</b>]] | ||
| − | | | + | |} |
<div style="margin-top:10px"> | <div style="margin-top:10px"> | ||
| − | |||
| − | |||
| − | |||
| − | |||
| − | <br /> | + | <div style="background: #FFFFFF; margin-top: 40px; font-weight: bold; line-height: 0.3em;letter-spacing:-0.08em;font-size:20px"><font color=#27408B face="Helvetica">INTRODUCTION</font></div> |
| − | <br /> | + | <br/> |
| + | The internet has become an indispensable tool in today’s business world. While it has fostered a tremendous amount of economic growth, it also introduced a series of profound vulnerabilities with a multitude of impacts: socially, economically and/or invading the privacy of an individual or organizations. In 2017, attacks can total up to $600 billion dollars, this alarming number has caught the world’s attention. It is believed that attackers will become increasingly creative with attack methods and increasingly destructive payloads that better target system vulnerabilities, with the luxury of anonymity and time. | ||
| + | <br/> | ||
| − | < | + | <div style="background: #FFFFFF; margin-top: 40px; font-weight: bold; line-height: 0.3em;letter-spacing:-0.08em;font-size:20px"><font color=#27408B face="Helvetica">MOTIVATION</font></div> |
| − | <br /> | + | <br/> |
| + | Cyber-attacks have made its way up to being one of the top 5 risk to global stability, amongst natural disasters, extreme weather, data fraud, and failure to address climate change. “Another growing trend is the use of cyberattacks to target critical infrastructure and strategic industrial sectors, raising fears that, in a worst-case scenario, attackers could trigger a breakdown in the systems that keep societies functioning. Over the years, there has been a shift from profit-motivated attacks to ones that aim to cause massive disruptions, such as the WannaCry ransomware campaign. Not knowing why or when attacks will strike, countries are left unprotected and unprepared. | ||
| − | <br /> | + | <br/> |
| + | <div style="background: #FFFFFF; margin-top: 40px; font-weight: bold; line-height: 0.3em;letter-spacing:-0.08em;font-size:20px"><font color=#27408B face="Helvetica">GOALS AND OBJECTIVES</font></div> | ||
| + | <br/> | ||
| + | * Understand and analyse the distribution of the Types, Sources and Impact of Breaches globally | ||
| + | *Understand the relationship between who's the culprit(source) and why did he do it(type) | ||
| + | * Compare the nature and impact of instances of reported breaches between countries | ||
| + | * Compare breaches between countries over time | ||
| − | |||
| + | <div style="background: #FFFFFF; margin-top: 40px; font-weight: bold; line-height: 0.3em;letter-spacing:-0.08em;font-size:20px"><font color=#27408B face="Helvetica">SELECTED DATASET</font></div> | ||
| − | |||
| − | {| class="wikitable" style=" | + | {| class="wikitable" style="position: center;" |
| − | + | |- | |
| − | ! | + | ! 1.Breach Level Index |
|- | |- | ||
| − | | | + | | Source : Gemalto, the world leader in digital security. |
| − | |||
| − | |||
| − | |||
|- | |- | ||
| − | | | + | | Purpose : Dataset is designed to provide a simple way to input publicly disclosed information on data breaches and calculate a score indicating breach severity. (https://breachlevelindex.com/) |
| − | |||
| − | |||
| − | |||
|- | |- | ||
| − | | | + | | |
| + | 1. Organization Breached | ||
| − | + | 2. Number of Records Breached | |
| − | + | 3. Date of Breach: | |
| − | + | 01/01/2013 - 29/06/2018 | |
| − | + | 4. Type of Breach | |
| + | -Nuisance (Email, Addresses, Affiliation) | ||
| + | -Account Access (Username, Passwords to websites/ social media) | ||
| + | -Financial Access (Bank Account Credentials) | ||
| + | -Identity Theft ( Information can be used to masquerade someone) | ||
| + | -Existential Data ( Info can be used to threaten business survival) | ||
| − | + | 5. Source of Breach: | |
| − | + | -Lost Device | |
| + | -Stolen Device | ||
| + | -Malicious Insider | ||
| + | -Malicious Outsider | ||
| + | -State Espionage | ||
| − | + | 6. Location: Country | |
| − | + | 7. Industry: | |
| − | + | -Technology, Other, Retail, Government, Healthcare, Education | |
| + | -Financial, Social Media, Hospitality, Entertainment, Insurance | ||
| + | -Non-profit, Industrial, Professional Services | ||
| − | + | 8. Risk Score: | |
| + | Log 10 ( Type of Data * Source of Breach * Whether Action was taken) | ||
|} | |} | ||
| − | |||
<p> | <p> | ||
</p> | </p> | ||
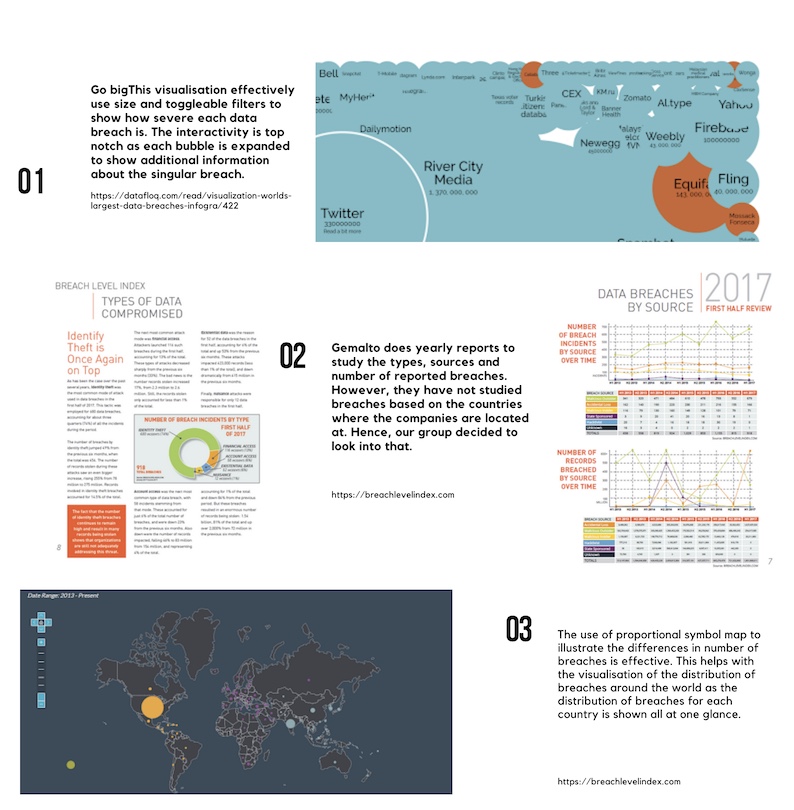
| − | <div style="background: #FFFFFF; margin-top: 40px; font-weight: bold; line-height: 0.3em;letter-spacing:-0.08em;font-size:20px"><font color=# | + | <div style="background: #FFFFFF; margin-top: 40px; font-weight: bold; line-height: 0.3em;letter-spacing:-0.08em;font-size:20px"><font color=#27408B face="Helvetica">BACKGROUND SURVEY OF RELATED WORKS</font></div> |
| + | |||
| + | [[File:7E0018ED-6DDB-4282-AFB6-1FFBEF6B8901.jpg|1000px|center]] | ||
| + | |||
| + | <div style="background: #FFFFFF; margin-top: 40px; font-weight: bold; line-height: 0.3em;letter-spacing:-0.08em;font-size:20px"><font color="#27408B" face="Helvetica">STORYBOARD</font></div> | ||
| + | |||
{| class="wikitable" style="background-color:#FFFFFF;" width="100%" | {| class="wikitable" style="background-color:#FFFFFF;" width="100%" | ||
| − | ! style="width:50%" | | + | ! style="width:50%" | Sketches |
| − | ! | + | ! Description |
| + | <b> </b> | ||
| + | (Possible users: Security management personnel from multinational corporations or governmental organization, who wishes to examine if their current effort and resources devoted to preventing cyber attacks are justified and effective as compared to other organizations of similar characteristics.) | ||
| + | |||
|- | |- | ||
| + | |||
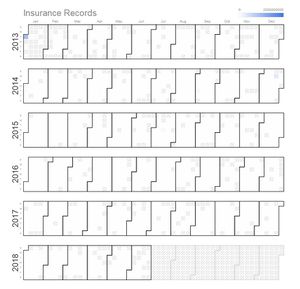
| style="text-align: center;" | <b> </b> | | style="text-align: center;" | <b> </b> | ||
| + | [[File:Heatmap.JPG|center|300px]] | ||
| + | <b> </b> | ||
| + | | | ||
| + | <h3>Breach Overview</h3> | ||
| + | |||
| + | '''Calendar Heatmap''' | ||
| + | |||
| + | To display time series data of the security breaches over the years, through a calendar heat map, by their respective industries. This way we can observe any spikes or anomalies within the same time period, across the different industries and take possible precautions for the future. Wouldn't it be interesting if we are able to spot correlations between the intended industry and the time of attack? | ||
| − | + | '''Technique: Filter''' | |
| + | Choose from dropdown box according to the industry to be visualised. | ||
| + | '''Technique: Tooltip''' | ||
| + | Mouse over to observe the details of the day, ie the number of records breached. | ||
|- | |- | ||
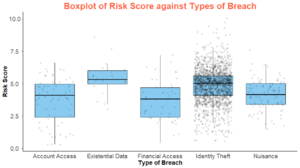
| − | | style="text-align: center;" | <b></b> | + | |
| + | | style="text-align: center;" | <b> </b> | ||
| + | [[File:Rplot.png|center|300px]] | ||
| + | <b> </b> | ||
| | | | ||
| + | '''Boxplot between type and source of breach''' | ||
| + | To understand across industries, what are the distribution of the types and sources of breaches, measured by the risk score or the number of records breached. Ever wondered for the healthcare industry, how susceptible are you to breaches used for financial access? The risk score shows you the extent of damage the risk could create, so that you can better prioritize on the attacks you want to defend yourself against. | ||
| + | |||
| + | '''Technique: Filter''' | ||
| + | Toggle between source or type of breach to observe the risk scores or number of records breached accordingly and choose the appropriate year from the slider or the desired industry | ||
| + | '''Technique: Tooltip''' | ||
| + | Mouse over to observe the details of individual records on the boxplot. | ||
|- | |- | ||
| − | + | ||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
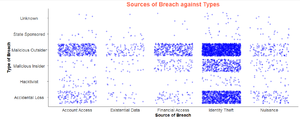
| style="text-align: center;" | <b> </b> | | style="text-align: center;" | <b> </b> | ||
| − | + | [[File:Boxplotoverview.png|center|300px]] | |
<b> </b> | <b> </b> | ||
| | | | ||
| − | + | ||
| + | '''Distribution of breaches''' | ||
| + | Source of breach over types of breach scatterplot. Distribution of the sources of attacks for each type of attacks and vice versa. Every wondered behind every breach used for financial gains, is it more likely to be done by a malicious insider or outsider? | ||
| + | |||
| + | '''Technique: Tooltip''' | ||
| + | Mouse over to observe the details of individual records | ||
|- | |- | ||
| − | |||
| − | <b></b> | + | | style="text-align: center;" | <b> </b> |
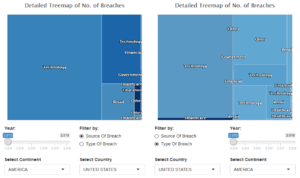
| + | [[File:Treemapblue.PNG|center|300px]] | ||
| + | <b> </b> | ||
| | | | ||
| + | <h3>Risk Comparison</h3> | ||
| + | |||
| + | '''Treemap''' | ||
| + | |||
| + | To understand in greater detail the characteristics of breaches affecting each country. Which industry is most threatened by breaches in a country and what are the causes of these breaches? Compare alone or between countries to gain more insights about the above! | ||
| − | + | '''Technique: Filter''' | |
| − | + | a) Radio button to filter by source or type of breach at the first layer | |
| − | + | b) Toggle which countries and/or continents to select for comparison | |
| − | + | c) Slider to select time period to be observed | |
| − | < | + | '''Technique: Tooltip''' |
| − | < | + | Tooltip when hovering the mouse over to show: |
| + | <ul> | ||
| + | <li>Type of Breach</li> | ||
| + | <li>Type of Industry</li> | ||
| + | <li>Source of Breach</li> | ||
| + | <li>Number of Records lost</li> | ||
| + | <li>Risk Score</li> | ||
| + | </ul> | ||
| + | |- | ||
| − | + | |} | |
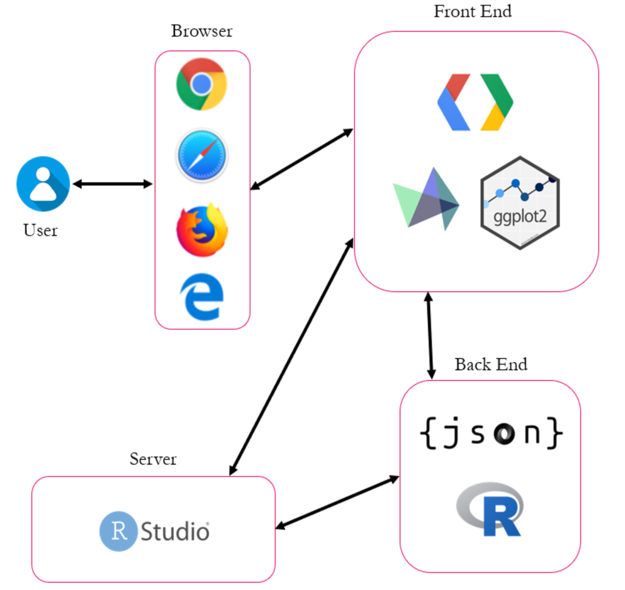
| + | <div style="background: #FFFFFF; margin-top: 40px; font-weight: bold; line-height: 0.3em;letter-spacing:-0.08em;font-size:20px"><font color="#27408B" face="Helvetica">ARCHITECTURE DIAGRAM</font> | ||
| + | </div> | ||
| − | <div style="background: #FFFFFF; margin-top: 40px; font-weight: bold; line-height: 0.3em;letter-spacing:-0.08em;font-size:20px"><font color=# | + | <br> |
| + | [[File:Ad.png|center|625px]] | ||
| + | <br> | ||
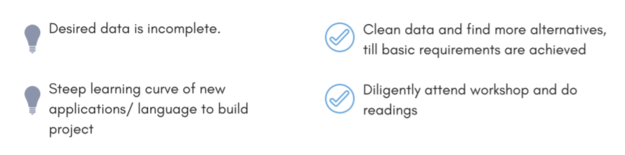
| + | <div style="background: #FFFFFF; margin-top: 40px; font-weight: bold; line-height: 0.3em;letter-spacing:-0.08em;font-size:20px"><font color="#27408B" face="Helvetica">KEY TECHNICAL CHALLENGES</font></div> | ||
| + | <br> | ||
| + | [[File:TechChallenges.png|center|625px]] | ||
| + | <br> | ||
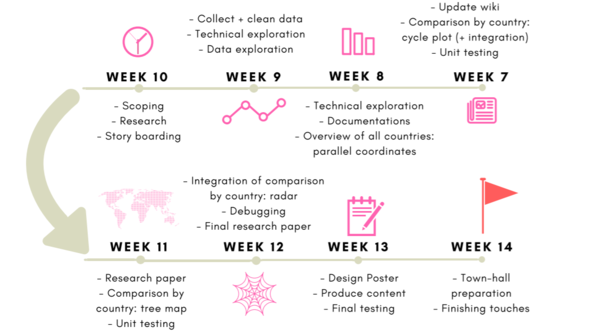
| + | <div style="background: #FFFFFF; margin-bottom:10px; margin-top: 40px; font-weight: bold; line-height: 0.3em;letter-spacing:-0.08em;font-size:20px"><font color=#27408B face="Helvetica">PROJECT TIMELINE</font></div> | ||
| + | <br> | ||
| + | [[File:Timeline.png|center|600px]] | ||
| + | <br> | ||
| + | <div style="background: #FFFFFF; margin-top: 40px; font-weight: bold; line-height: 0.3em;letter-spacing:-0.08em;font-size:20px"><font color=#27408B face="Helvetica">REFERENCES</font></div> | ||
| + | 1. https://www.csa.gov.sg/news/press-releases/cyber-threats-in-singapore-grew-in-2017-mirroring-global-trends | ||
| + | <br> | ||
| + | 2. https://www.todayonline.com/singapore/cyber-threats-singapore-go-phishing-attacks-see-biggest-jump | ||
| + | <br> | ||
| + | 3. https://www.mcafee.com/enterprise/en-us/solutions/lp/economics-cybercrime.html | ||
| + | <br> | ||
| + | 4. http://bl.ocks.org/mthh/7e17b680b35b83b49f1c22a3613bd89f | ||
| + | <br> | ||
| + | 5. http://www.perceptualedge.com/articles/guests/intro_to_cycle_plots.pdf | ||
| + | <br> | ||
| + | <br> | ||
| + | Data Sources: | ||
| + | <br> | ||
| + | http://hdr.undp.org/en/data# | ||
| + | <br> | ||
| + | https://datacatalog.worldbank.org/dataset/harmonized-list-fragility-conflict-and-violence-countries | ||
| + | <br> | ||
| + | http://databank.worldbank.org/data/reports.aspx?source=2&series=IT.NET.USER.ZS# | ||
| + | <br><br> | ||
| − | <div style="background: #FFFFFF; margin-top: 40px; font-weight: bold; line-height: 0.3em;letter-spacing:-0.08em;font-size:20px"><font color=# | + | <div style="background: #FFFFFF; margin-top: 40px; font-weight: bold; line-height: 0.3em;letter-spacing:-0.08em;font-size:20px"><font color=#27408B face="Helvetica">COMMENTS</font></div> |
Feel free to comments, suggestions and feedbacks to help us improve our project!:D | Feel free to comments, suggestions and feedbacks to help us improve our project!:D | ||
| − | + | <div style="background: #FFFFFF; margin-top: 40px; font-weight: bold; line-height: 0.3em;letter-spacing:-0.08em;font-size:20px"><font color=#27408B face="Helvetica">Version 1 of proposal</font></div> | |
| + | [[File:Proposal The Defenders Version 1.pdf|thumb]] | ||
Latest revision as of 17:20, 25 November 2018
The internet has become an indispensable tool in today’s business world. While it has fostered a tremendous amount of economic growth, it also introduced a series of profound vulnerabilities with a multitude of impacts: socially, economically and/or invading the privacy of an individual or organizations. In 2017, attacks can total up to $600 billion dollars, this alarming number has caught the world’s attention. It is believed that attackers will become increasingly creative with attack methods and increasingly destructive payloads that better target system vulnerabilities, with the luxury of anonymity and time.
Cyber-attacks have made its way up to being one of the top 5 risk to global stability, amongst natural disasters, extreme weather, data fraud, and failure to address climate change. “Another growing trend is the use of cyberattacks to target critical infrastructure and strategic industrial sectors, raising fears that, in a worst-case scenario, attackers could trigger a breakdown in the systems that keep societies functioning. Over the years, there has been a shift from profit-motivated attacks to ones that aim to cause massive disruptions, such as the WannaCry ransomware campaign. Not knowing why or when attacks will strike, countries are left unprotected and unprepared.
- Understand and analyse the distribution of the Types, Sources and Impact of Breaches globally
- Understand the relationship between who's the culprit(source) and why did he do it(type)
- Compare the nature and impact of instances of reported breaches between countries
- Compare breaches between countries over time
| 1.Breach Level Index |
|---|
| Source : Gemalto, the world leader in digital security. |
| Purpose : Dataset is designed to provide a simple way to input publicly disclosed information on data breaches and calculate a score indicating breach severity. (https://breachlevelindex.com/) |
|
1. Organization Breached 2. Number of Records Breached 3. Date of Breach: 01/01/2013 - 29/06/2018 4. Type of Breach -Nuisance (Email, Addresses, Affiliation) -Account Access (Username, Passwords to websites/ social media) -Financial Access (Bank Account Credentials) -Identity Theft ( Information can be used to masquerade someone) -Existential Data ( Info can be used to threaten business survival) 5. Source of Breach: -Lost Device -Stolen Device -Malicious Insider -Malicious Outsider -State Espionage 6. Location: Country 7. Industry: -Technology, Other, Retail, Government, Healthcare, Education -Financial, Social Media, Hospitality, Entertainment, Insurance -Non-profit, Industrial, Professional Services 8. Risk Score: Log 10 ( Type of Data * Source of Breach * Whether Action was taken) |
| Sketches | Description
(Possible users: Security management personnel from multinational corporations or governmental organization, who wishes to examine if their current effort and resources devoted to preventing cyber attacks are justified and effective as compared to other organizations of similar characteristics.) |
|---|---|
|
|
Breach OverviewCalendar Heatmap To display time series data of the security breaches over the years, through a calendar heat map, by their respective industries. This way we can observe any spikes or anomalies within the same time period, across the different industries and take possible precautions for the future. Wouldn't it be interesting if we are able to spot correlations between the intended industry and the time of attack? Technique: Filter Choose from dropdown box according to the industry to be visualised. Technique: Tooltip Mouse over to observe the details of the day, ie the number of records breached. |
|
|
Boxplot between type and source of breach To understand across industries, what are the distribution of the types and sources of breaches, measured by the risk score or the number of records breached. Ever wondered for the healthcare industry, how susceptible are you to breaches used for financial access? The risk score shows you the extent of damage the risk could create, so that you can better prioritize on the attacks you want to defend yourself against. Technique: Filter Toggle between source or type of breach to observe the risk scores or number of records breached accordingly and choose the appropriate year from the slider or the desired industry Technique: Tooltip Mouse over to observe the details of individual records on the boxplot. |
|
|
Distribution of breaches Source of breach over types of breach scatterplot. Distribution of the sources of attacks for each type of attacks and vice versa. Every wondered behind every breach used for financial gains, is it more likely to be done by a malicious insider or outsider? Technique: Tooltip Mouse over to observe the details of individual records |
|
|
Risk ComparisonTreemap To understand in greater detail the characteristics of breaches affecting each country. Which industry is most threatened by breaches in a country and what are the causes of these breaches? Compare alone or between countries to gain more insights about the above! Technique: Filter a) Radio button to filter by source or type of breach at the first layer b) Toggle which countries and/or continents to select for comparison c) Slider to select time period to be observed Technique: Tooltip Tooltip when hovering the mouse over to show:
|
1. https://www.csa.gov.sg/news/press-releases/cyber-threats-in-singapore-grew-in-2017-mirroring-global-trends
2. https://www.todayonline.com/singapore/cyber-threats-singapore-go-phishing-attacks-see-biggest-jump
3. https://www.mcafee.com/enterprise/en-us/solutions/lp/economics-cybercrime.html
4. http://bl.ocks.org/mthh/7e17b680b35b83b49f1c22a3613bd89f
5. http://www.perceptualedge.com/articles/guests/intro_to_cycle_plots.pdf
Data Sources:
http://hdr.undp.org/en/data#
https://datacatalog.worldbank.org/dataset/harmonized-list-fragility-conflict-and-violence-countries
http://databank.worldbank.org/data/reports.aspx?source=2&series=IT.NET.USER.ZS#
Feel free to comments, suggestions and feedbacks to help us improve our project!:D