ISSS608 2017-18 T3 Assign Aakanksha Kumari Q3
Unraveling the Secrets of Kasios : VAST Mini Challenge 3
|
|
|
|
|
|
|
|
Using the combined group of suspected bad actors, you created in question 2, show the interactions within the group over time.
|
Contents
The Story So Far
The Kasios International over the course of two and half years have maintained nearly same communicationa volumne and purchase pattern, which implies that the organization have not grown or shrunk significantly. But on closer analysis we found out with each year, the new employees were being hired, and there is constant shuffling of human resource. Kasios have grow significant change in personnels, with numnber of same employees each month decreasing. Intially we began with certain suspicious transactions (purchaes and communication) as provided by our informer. Later as we continued our analysis, othe key players, closely associated to employees making suspicious communication were identified. Using network analysis and eigenvector centrality (filter value > 0.4), nodes connected to influential nodes (in this case, suspicious employees) more than other non-influential nodes(non suspicious employees), can be identified. So by following the above startegy following are list of old and new suspicious players. Original Suspicious Employess Augusta Sharp, Tobi Gatlin ,Patrick Lane, Melita Scarpaci, Rosalia Larroque, Glen Grant ,Meryl Pastuch, Dylan Ballard, May Burton, Kerstin Belveal, Alex Hall, Refugio Orrantia, Jose Ringwald, Julie Tierno, Richard Fox, Lizbeth Jindra, Ramiro Gault, Sara Ballard, Jenice Savaria, Lindsy Henion New Suspicious Employees So now our focus is on these 26 key players, as discussed in Q2 Main Tasks in this section
|
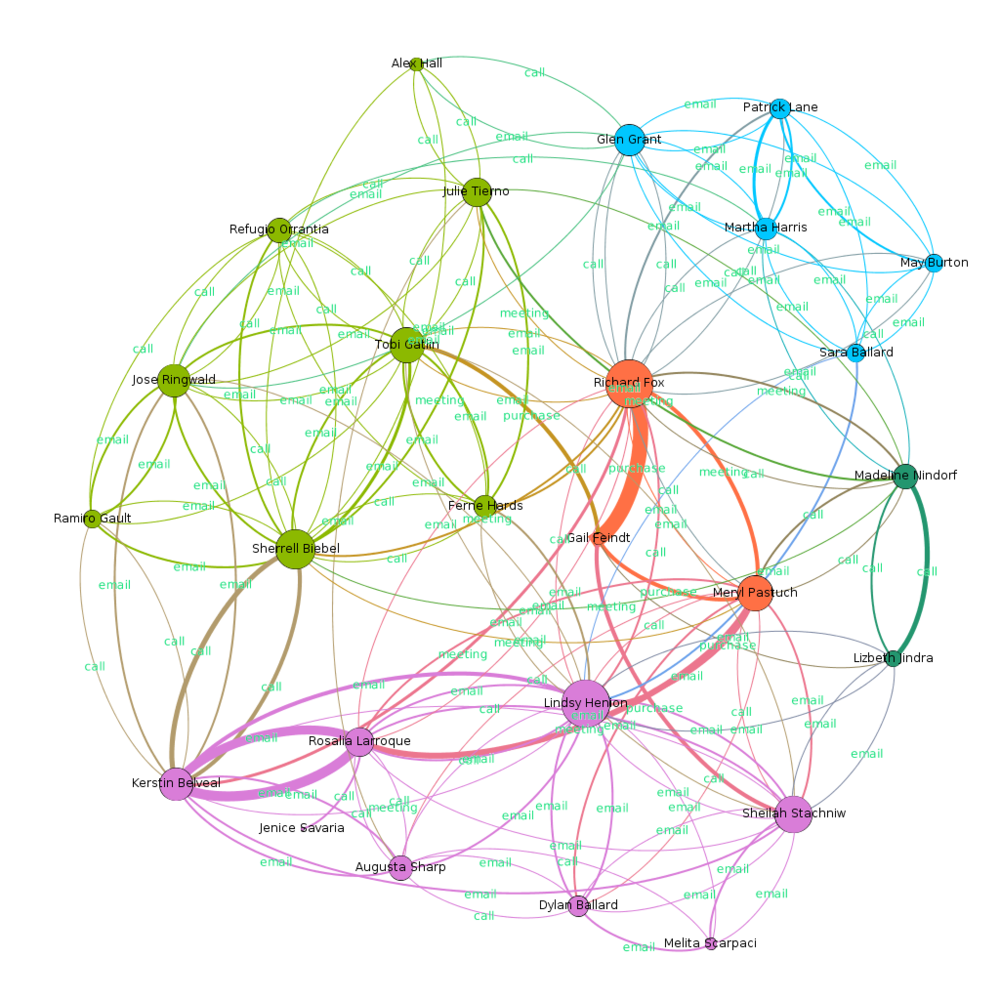
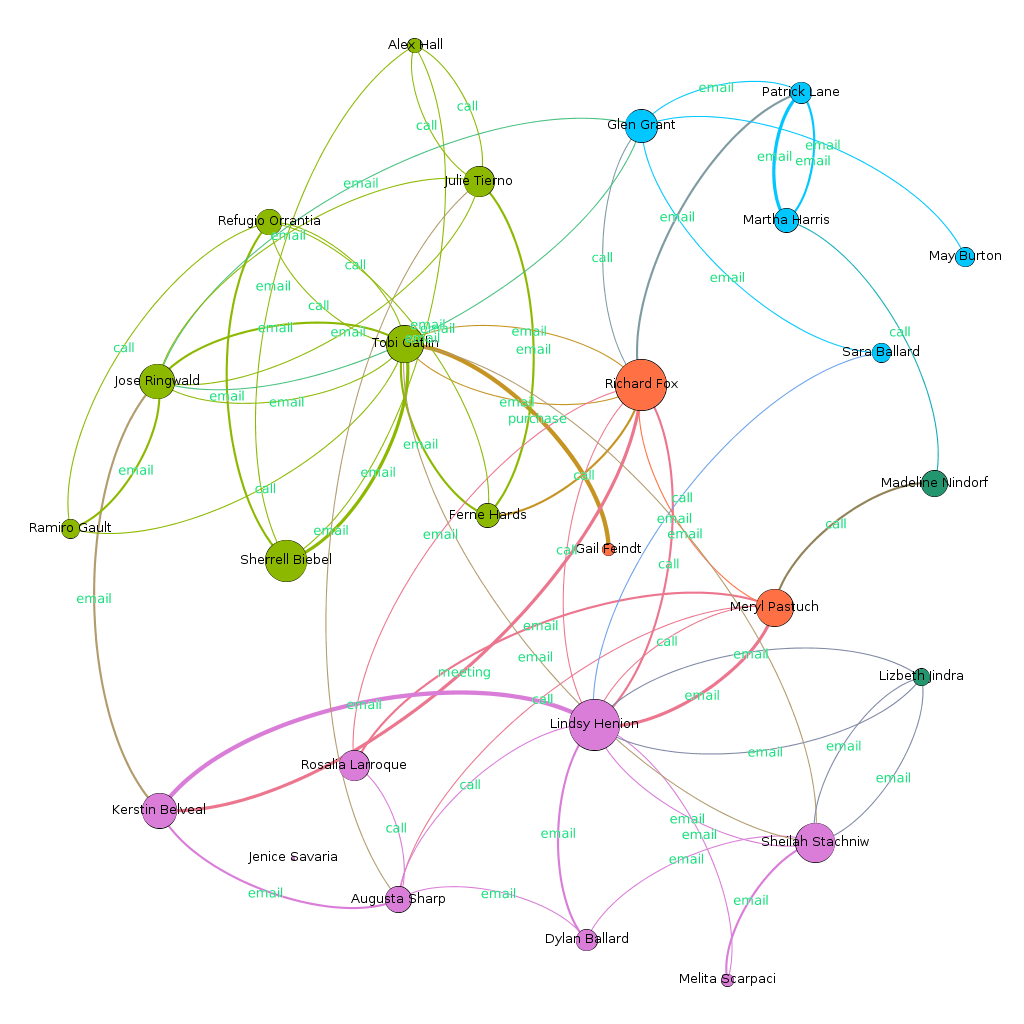
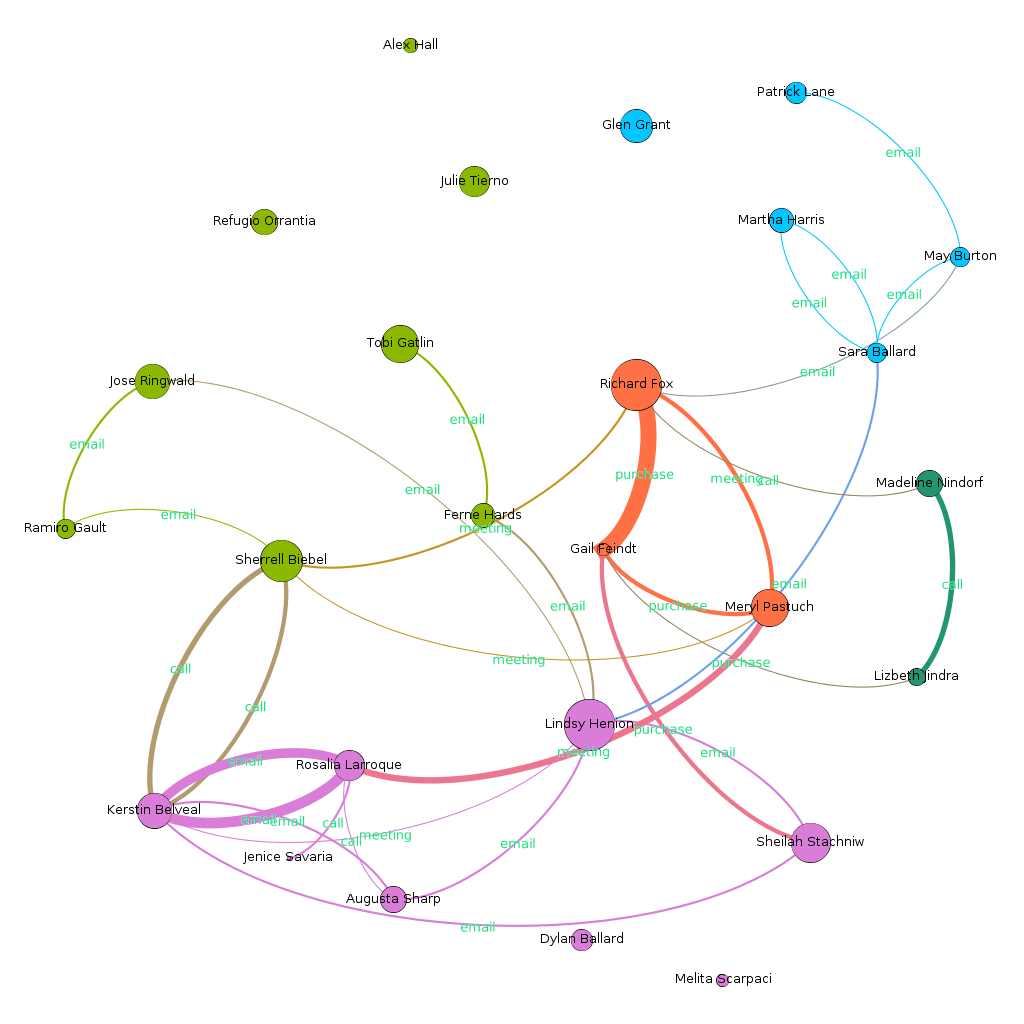
The Combined Communication Picture
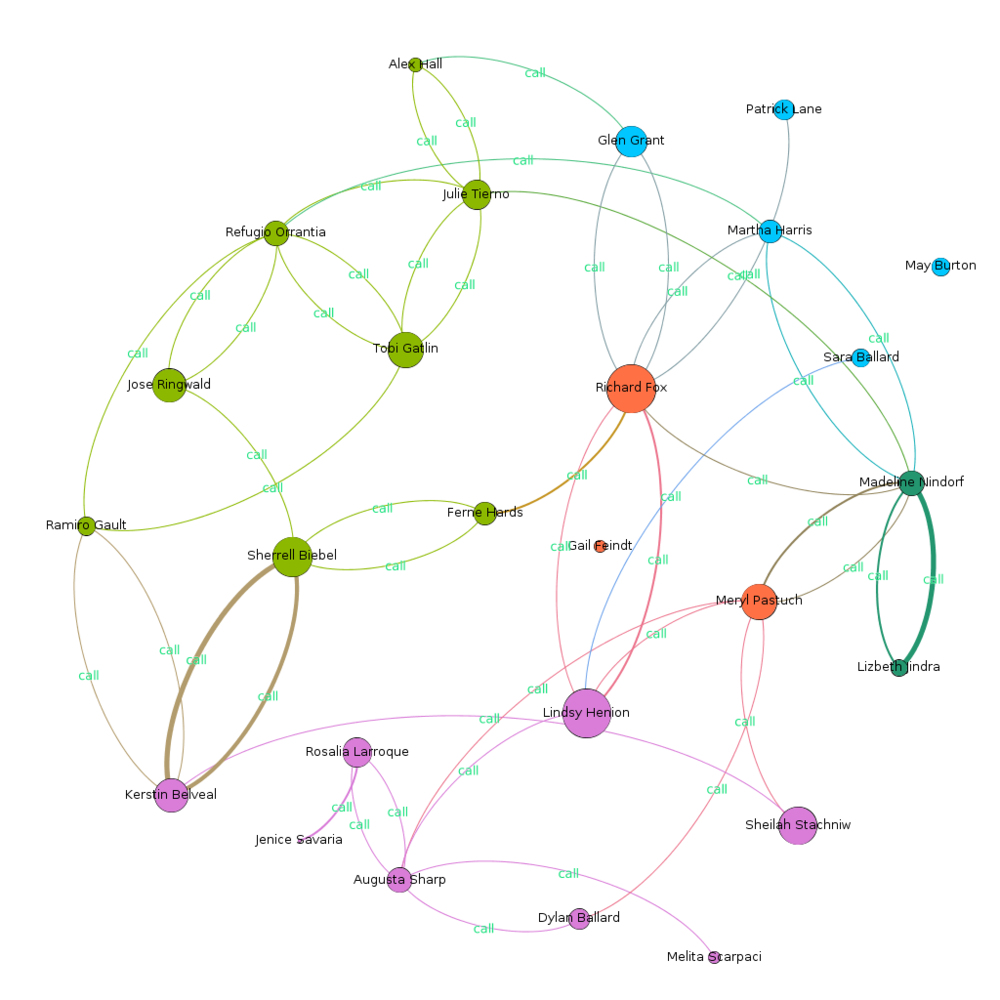
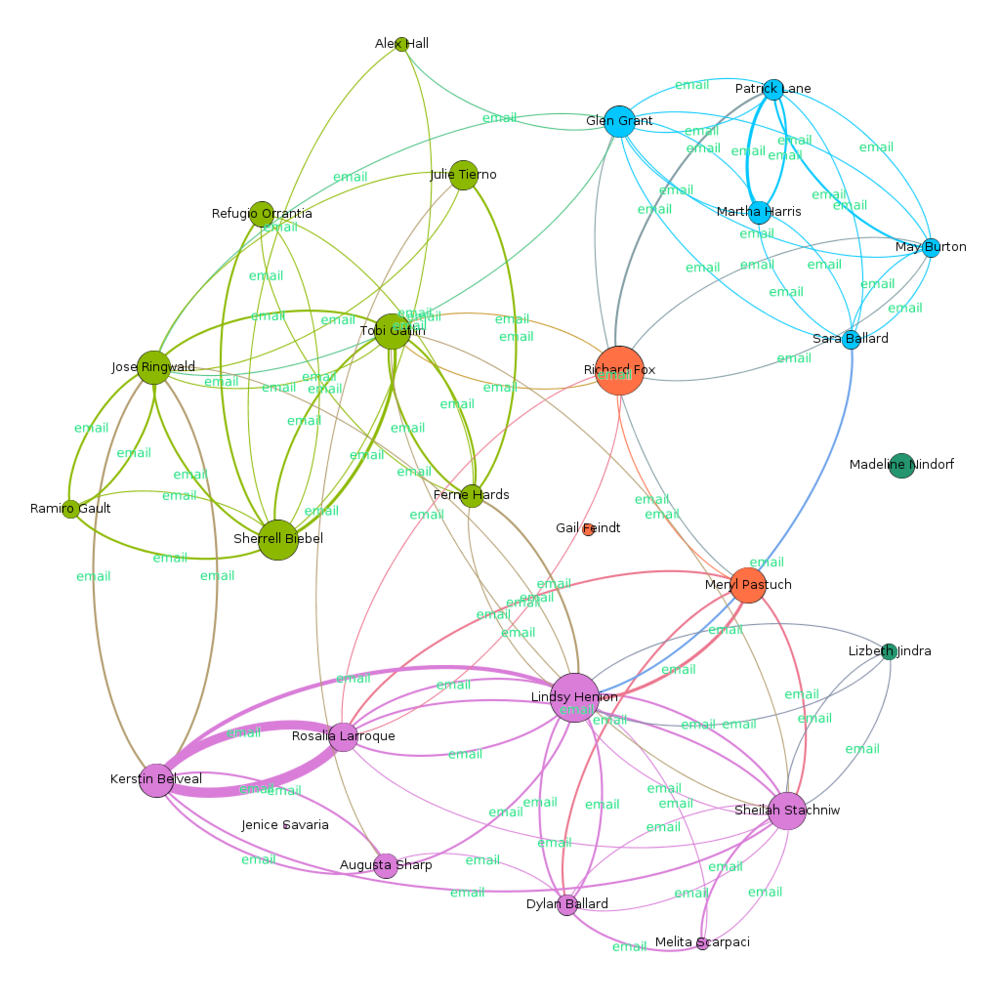
Using modularity algoithm, and assigning distinct class color, the graph is clustered into 5 classes. This helps in better visualization, and also identifying key players in each cluster. All the clusters are discusses individually later. What can we learn
|
Clusters Discussed Individually
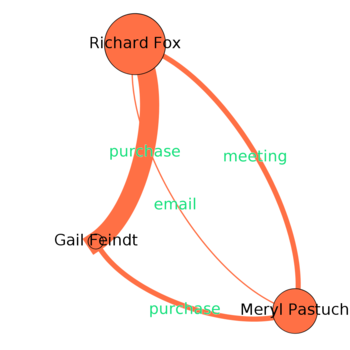
Cluster 1 (Red)
Main Channel of Interaction: Purchase |
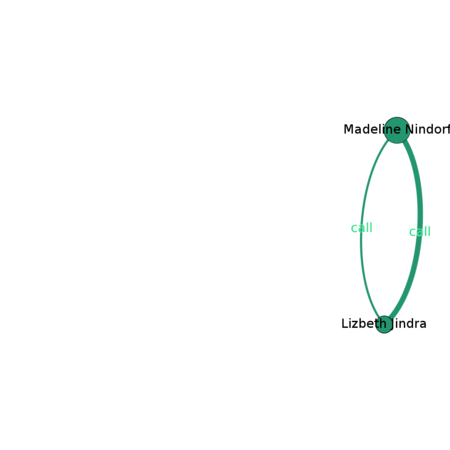
Cluster 2 (Dark Green) (Small cluster, connected through call)
Main Channel of Interaction: Call |
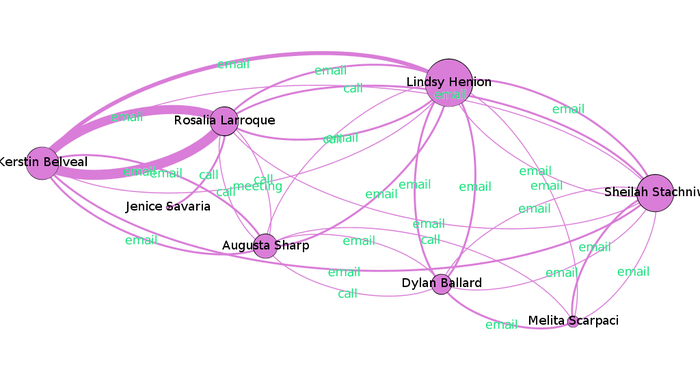
Cluster 3 (Pink)
Main Channel of Interaction: Email, Call |
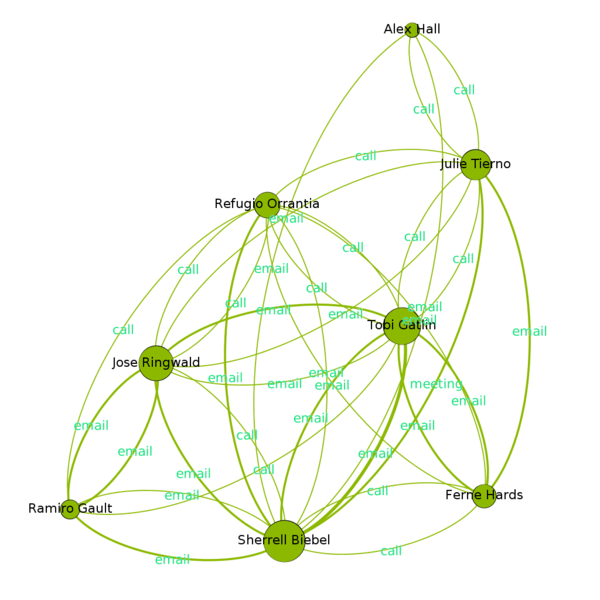
Cluster 4 (Light Green)
Main Channel of Interaction: Email, Call |
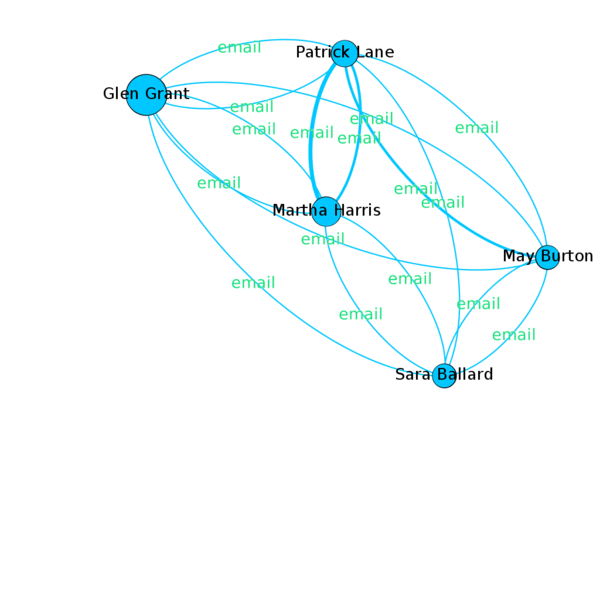
Cluster 5 (Blue)
Main Channel of Interaction: Email |
Group composition over different activities
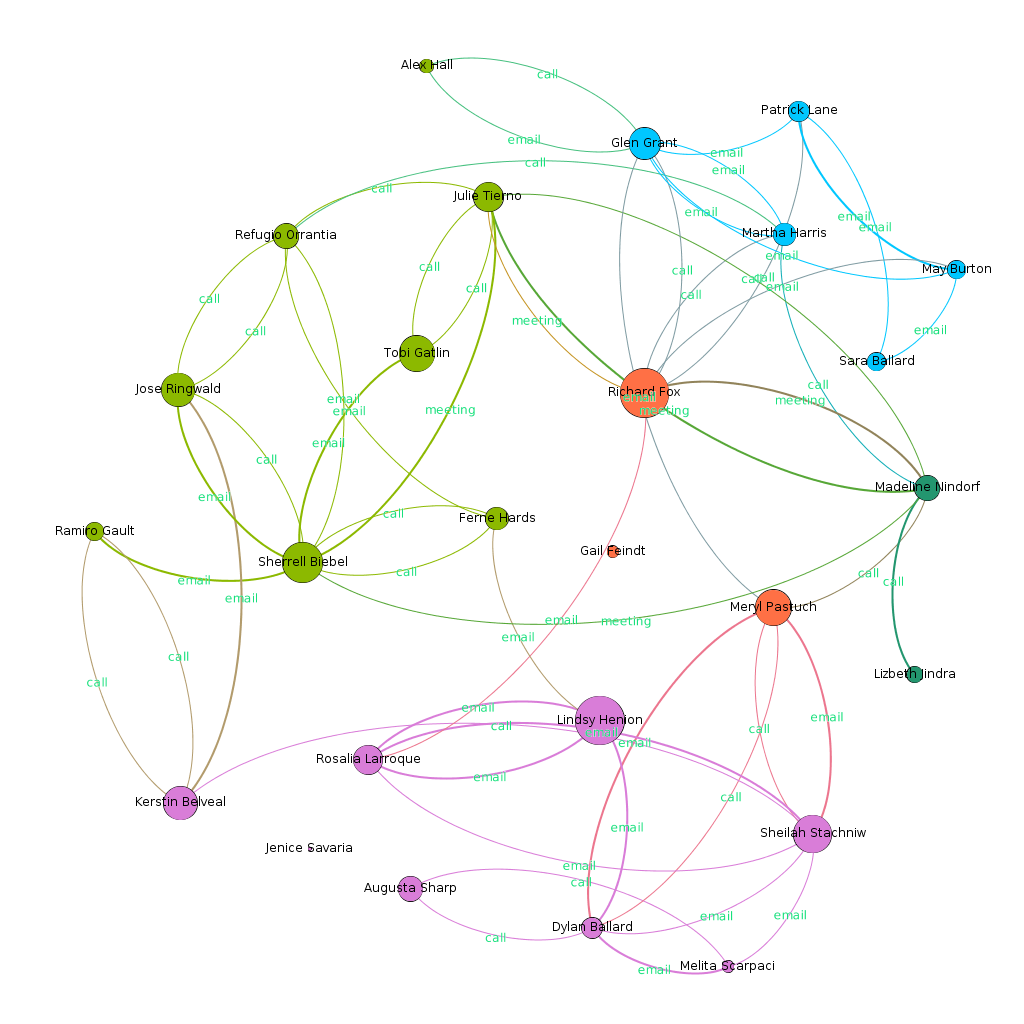
Calls
Emails
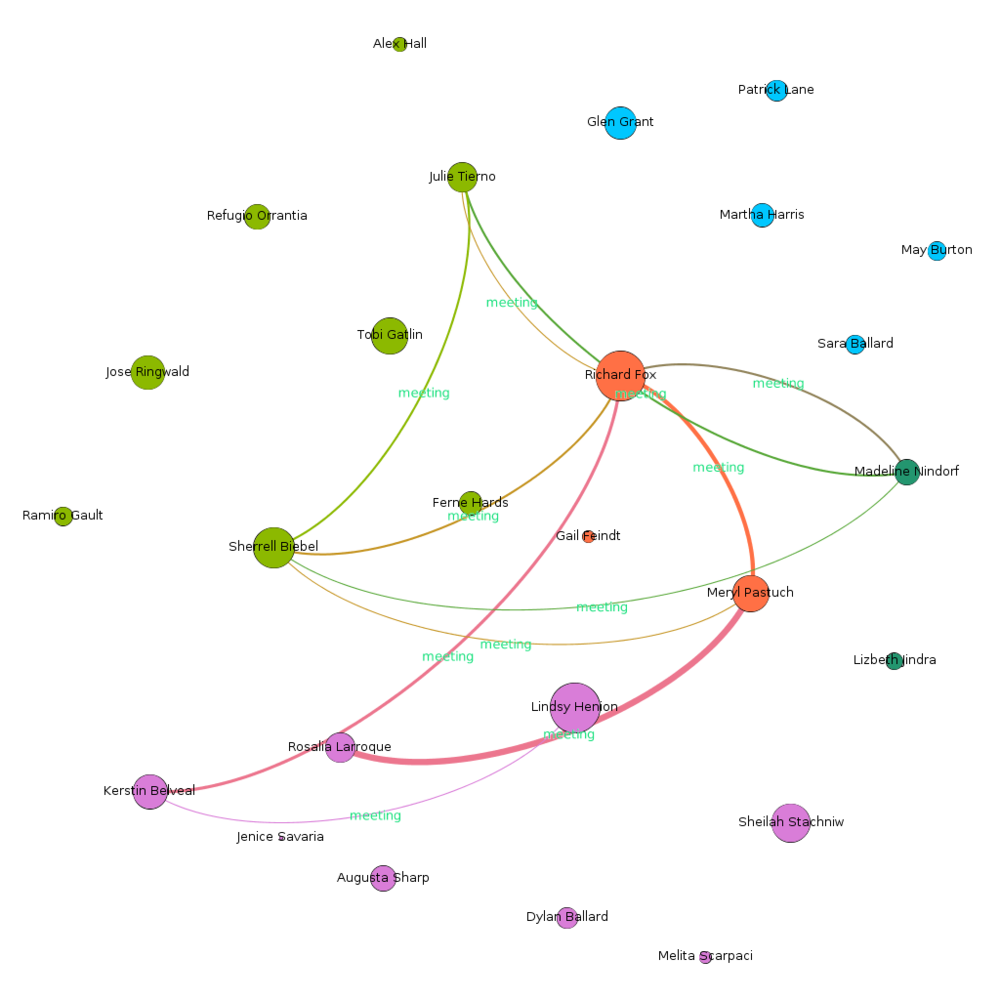
Meetings
Meetings shows the most interesting pattern.
- Meetings mostly happen inter cluster.
- Blue Cluster, did not participate in any meetings. Which clears them of any suspicion.
- Meetings primarly connect Red cluster, yet again.
- Gail Feindt is again not connected to any employee through meetings.
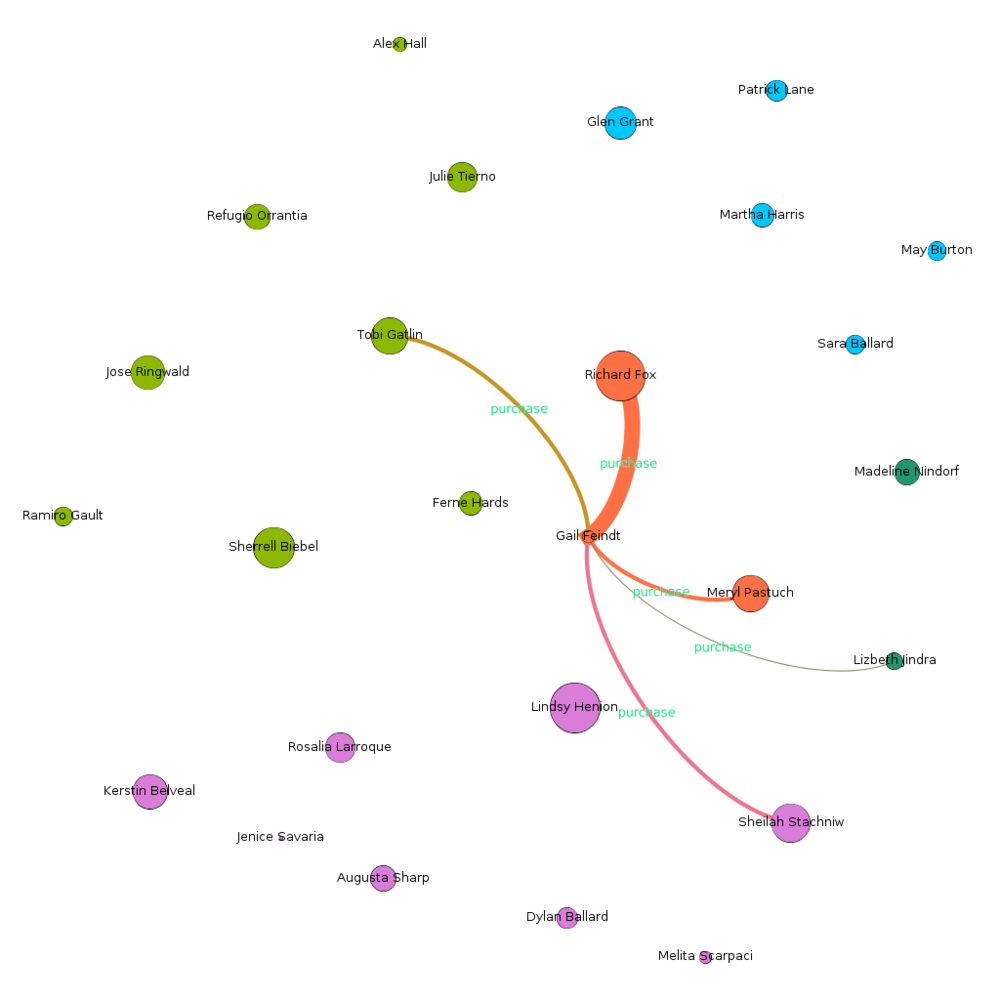
Purchases
Purchases (combined with meetings) hints towards source of all suspicion.
|
Group’s Interactions Change Over Time
Purchases (combined with meetings) hints towards source of all suspicion.
|
Conclusion
|
Narrowed down suspicious employees (12)
Gail Feindt, Richard Fox, Meryl Pastuch, Lizbeth Jindra, Madeline Nindorf, Lindsy Henion, Sheilah Stachniw, Kerstin Belveal, Sherrell Biebel, Tobi Gatlin, Julie Tierno, Glen Grant