ISSS608 2017-18 T3 Assign Vishal Badrinarayanan Question4
|
|
|
|
|
|
|
|
|
- Data for Q4:
- The data for this is obtained from the other suspicious purchases details which was provided by the insider .
- WE use that data and filtered all the transactions from the total dataset that we created based on the source and target node .
- We then used this data to plot in gephi giving both static and dynamic plots.
- We used modularity class for forming different clusters and gave betweenness centrality for the size of the nodes.
- The edges are represented by the E-types .
- Here Red is Purchases , purple is mails and green is calls.
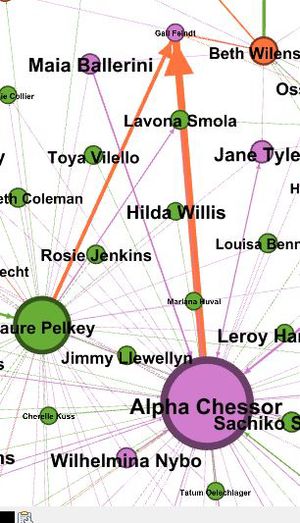
We used the modularity class and we found that in this dataset also there is one node which has the maximum influence like Richard fox .Here also like the initial suspicious list there are some specific people who are involved with purchases.In this graph there are more than two people involved in purchases compared to last question.The smaller groups formd usually interact mainly within their clusters.
From the graph we can find that Aplha Chessor is the most influential node and after that it is Laure Pelkey. These two nodes are connected with a lot of other nodes not in their cluster. Gail Feindt is used as the main person for any kind of purchases.
Most of the orders for the purchases is from Laura and Alpha who are the two most influential people in the network.
Example of Suspicious Activity:
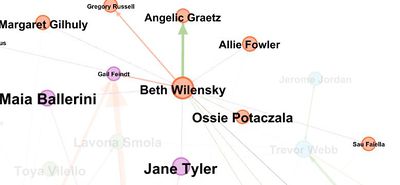
- Gail Fendt is not present in the suspicious list so we can analyse other nodes who are involved in purchase activities.
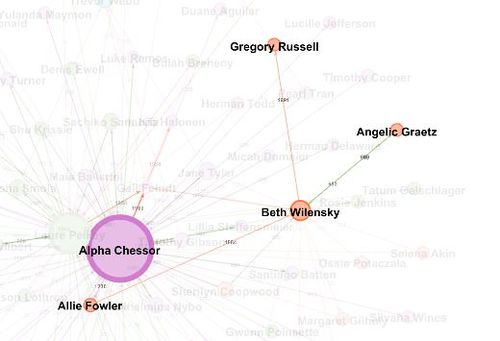
We can tell from this picture Ben Wilensky has the highest betweenness and all the purchases also go through him. We find that there are orders to Gregory Russell which can make other nodes like Ben Wilensky could be involved in suspicious transactions.
Also there are purchase transaction from Alli Fowler to Ben Hilensky and some other purchase orders.
- There is only one transaction for Carlos Morris from Laure Pelkey which is unusual as most of the purchase from her is sent to Gild Feint.
- There are purchase sent from Alpha and Laure which might be suspicious as they are in the suspicious list.
Some transaction which are involved in suspicious transactions and can be shown as a temporal pattern are:
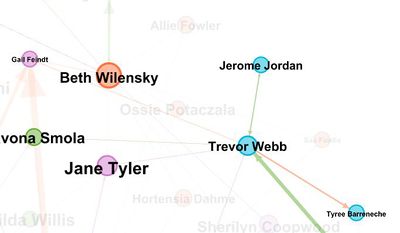
- 1st Transaction - Pearl Tran – Tyree Barreneche -
- 2nd Transaction - Tyree Barrenche – Trevor web –
- 1st transaction - Timothy Gibson / Sherilyn Cooper / Lilla &ndash to Alpha Cessor
- 2nd Transaction - Alpha Cessor to Kia Halonen.
- We need to check the tramsaction as in the first message to alpha cessor all of them sent at a similar time , so we cant decide for sure who has sent the message .
- We can find if their patterns and decide who can be the source.
- Since Alpha Cessor I sinvolved in transaction all the others might also be involved in suspicious activites.
- In the first question Timothy Gibson was involved there and she is involved here as well.