Difference between revisions of "ISSS608 2017-18 T3 Assign Aakanksha Kumari Data Preparation"
Jump to navigation
Jump to search
| Line 54: | Line 54: | ||
There are four data files that contain information about individuals that the Insider has indicated as suspicious: </big></div> | There are four data files that contain information about individuals that the Insider has indicated as suspicious: </big></div> | ||
[[File:D2.PNG|1000px|frameless|center]] | [[File:D2.PNG|1000px|frameless|center]] | ||
| + | |||
| + | <div style="font-family:Palatino Linotype; border-radius: 1px "> <big> | ||
| + | All provided data files have the same format. The data are provided in comma-separated format with four columns: </big></div> | ||
|} | |} | ||
Revision as of 23:33, 7 July 2018
MC Challenge 3
|
|
|
|
|
|
|
|
|
Data Set
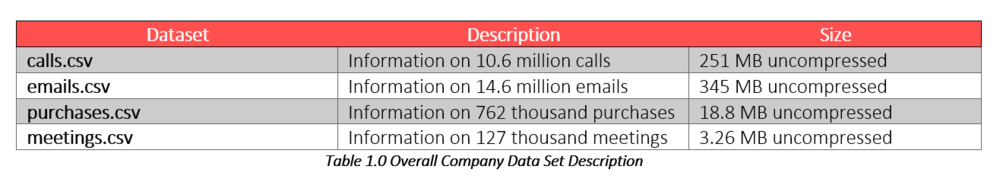
The Kasios Insider has provided data from across the company. There are call records, emails, purchases, and meetings. The data only includes the source of each transaction, the recipient (destination), and the time of the transaction. Contents of emails or phone calls are not available.
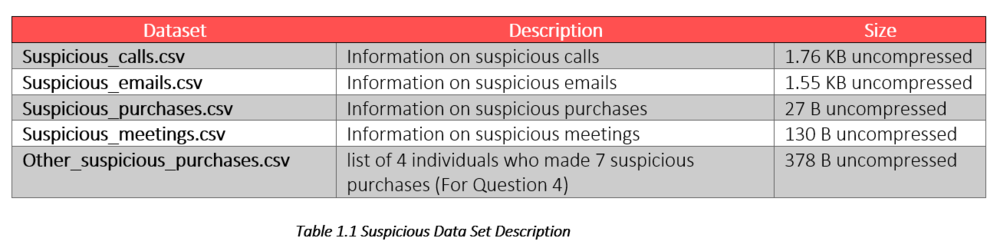
There are four data files that contain information about individuals that the Insider has indicated as suspicious:
All provided data files have the same format. The data are provided in comma-separated format with four columns:
|