Difference between revisions of "ISSS608 2017-18 T3 Assign Aakanksha Kumari Q4"
Jump to navigation
Jump to search
| (3 intermediate revisions by the same user not shown) | |||
| Line 2: | Line 2: | ||
<div style="background:#DC143C; border:#DC143C; padding-left:15px; text-align:center;"> | <div style="background:#DC143C; border:#DC143C; padding-left:15px; text-align:center;"> | ||
| − | <font size = 5; color="#FFFFFF"><span style="font-family:Century Gothic;"> | + | <font size = 5; color="#FFFFFF"><span style="font-family:Century Gothic;">Unraveling the Secrets of Kasios : VAST Mini Challenge 3</span></font> |
</div> | </div> | ||
<!--MAIN HEADER --> | <!--MAIN HEADER --> | ||
| Line 29: | Line 29: | ||
; | ; | ||
[[ISSS608 2017-18 T3 Assign Aakanksha Kumari_Q4| <font color="#FFFFFF">Question 4</font>]] | [[ISSS608 2017-18 T3 Assign Aakanksha Kumari_Q4| <font color="#FFFFFF">Question 4</font>]] | ||
| − | |||
| − | |||
| − | |||
| − | |||
| style="font-family:Century Gothic; font-size:100%; solid #DC143C; background:#DC143C; text-align:center;" width="14.3%" | | | style="font-family:Century Gothic; font-size:100%; solid #DC143C; background:#DC143C; text-align:center;" width="14.3%" | | ||
| Line 46: | Line 42: | ||
<big>'''''The insider has provided a list of purchases that might indicate illicit activity elsewhere in the company. Using the structure of the first group noted by the insider as a model can you find any other instances of suspicious activities in the company? Are there other groups that have structure and activity similar to this one? Who are they? Each of the suspicious purchases could be a starting point for your search. Provide examples of up to two other groups you find that appear suspicious and compare their structure with the structure of the first group. '''''</big> </div> | <big>'''''The insider has provided a list of purchases that might indicate illicit activity elsewhere in the company. Using the structure of the first group noted by the insider as a model can you find any other instances of suspicious activities in the company? Are there other groups that have structure and activity similar to this one? Who are they? Each of the suspicious purchases could be a starting point for your search. Provide examples of up to two other groups you find that appear suspicious and compare their structure with the structure of the first group. '''''</big> </div> | ||
|} | |} | ||
| + | |||
| + | === Structure of Previous Transactions === | ||
| + | <div style="font-family:Palatino Linotype; border-radius: 1px "> <big> | ||
| + | To understand the structure of newly provided list, we must decode complete structure of early transaction. </big> </div> | ||
| + | |||
| + | [[File:Transaction structure.png|800px|frameless|center]] | ||
| + | |||
| + | {| class="wikitable" | ||
| + | |- | ||
| + | |<div style="font-family:Palatino Linotype; border-radius: 1px "> <big> | ||
| + | Rosalia Larroque --> meeting --> Meryl Pastuch (2017-09-03 03:18:53) <br> | ||
| + | Rosalia Larroque --> email--> Kerstin Belveal (2017-09-18 04:33:43) <br> | ||
| + | Rosalia Larroque --> call --> Jenice Savaria, 2017-09-19 22:05:33 <br> | ||
| + | Rosalia Larroque --> purchase --> Jenice Savaria, 2017-09-20 14:45:33 <br> | ||
| + | |||
| + | Interesting thing to note is suspicious transaction start with meeting with Meryl Pastuch, followed by series of email and call communication between Rosalia and Kerstin. At end Rosalia Larroque purchases. </big> </div> | ||
| + | |} | ||
| + | |||
| + | === List of Other Suspicious Transactions === | ||
| + | [[File:Other suspicious transaction.png|600px|frameless|center]] | ||
| + | |||
| + | ==== Other Similar Transactions ==== | ||
| + | |||
| + | {| class="wikitable" | ||
| + | |- | ||
| + | |<div style="font-family:Palatino Linotype; border-radius: 1px "> <big> | ||
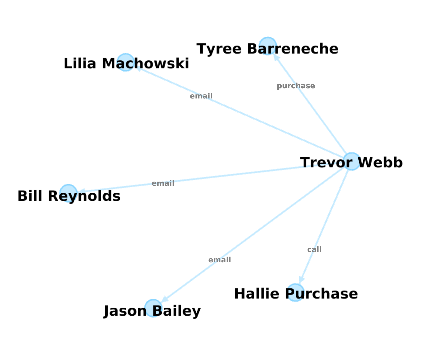
| + | '''Case of Trevor Webb''' <br> | ||
| + | *call, 2016-11-09 20:01:28, Trevor Webb, Hallie Purchase | ||
| + | *email, 2016-12-22 01:23:27, Trevor Webb, Lilia Machowski | ||
| + | *purchase, 2017-01-16 09:35:09, Trevor Webb, Tyree Barreneche | ||
| + | *email, 2017-07-16 16:00:35 2017, Trevor Webb, Jason Bailey | ||
| + | *purchase, 2017-07-24 19:49:03, Trevor Webb, Tyree Barreneche | ||
| + | *email, 2017-07-26 04:57:33, Trevor Webb, Bill Reynolds | ||
| + | </big> </div> | ||
| + | |} | ||
| + | |||
| + | [[File:Trevor webb.png|500px|frameless|center]] | ||
| + | |||
| + | {| class="wikitable" | ||
| + | |- | ||
| + | |<div style="font-family:Palatino Linotype; border-radius: 1px "> <big> | ||
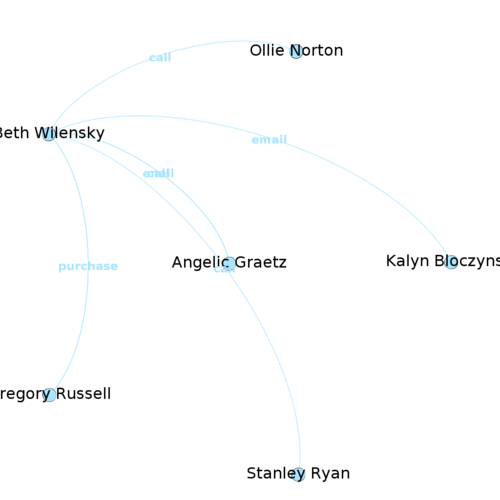
| + | '''Case of Beth Wilensky''' <br> | ||
| + | *call,2017-11-15 23:05:20,Beth Wilensky,Ollie Norton | ||
| + | *email,2017-11-23 02:53:33,Beth Wilensky,Kalyn Bloczynski | ||
| + | *purchase,2017-12-12 02:26:32,Beth Wilensky,Gregory Russell | ||
| + | *call,2017-12-12 02:26:32,Beth Wilensky,Stanley Ryan | ||
| + | *call,2017-05-14 03:51:02,Beth Wilensky,Angelic Graetz | ||
| + | *purchase,2017-06-03 03:51:02,Beth Wilensky,Gregory Russell | ||
| + | *enail,2017-06-03 03:51:02,Beth Wilensky,Angelic Graetz | ||
| + | </big> </div> | ||
| + | |} | ||
| + | |||
| + | [[File:Beth wilensky.png|500px|frameless|center]] | ||
Latest revision as of 13:26, 8 July 2018
Unraveling the Secrets of Kasios : VAST Mini Challenge 3
|
|
|
|
|
|
|
|
The insider has provided a list of purchases that might indicate illicit activity elsewhere in the company. Using the structure of the first group noted by the insider as a model can you find any other instances of suspicious activities in the company? Are there other groups that have structure and activity similar to this one? Who are they? Each of the suspicious purchases could be a starting point for your search. Provide examples of up to two other groups you find that appear suspicious and compare their structure with the structure of the first group.
|
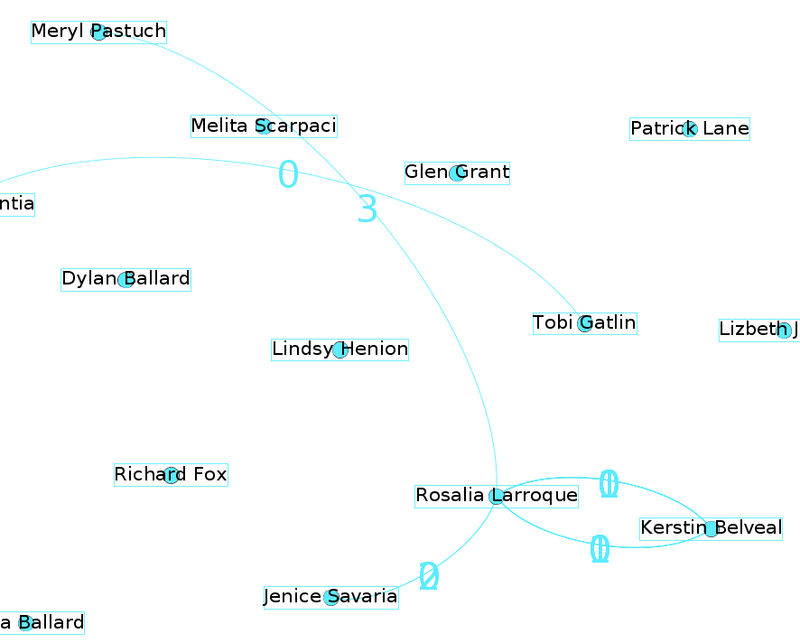
Structure of Previous Transactions
To understand the structure of newly provided list, we must decode complete structure of early transaction.
Rosalia Larroque --> meeting --> Meryl Pastuch (2017-09-03 03:18:53) |
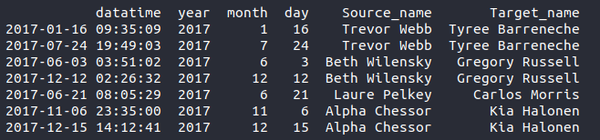
List of Other Suspicious Transactions
Other Similar Transactions
Case of Trevor Webb
|
Case of Beth Wilensky
|