Difference between revisions of "AssignYL Explore"
Jump to navigation
Jump to search
| (3 intermediate revisions by the same user not shown) | |||
| Line 22: | Line 22: | ||
| style="font-family:Segoe UI light; font-size:100%; solid #FFFFFF; background:#000000; text-align:center;" width="20.00%" | | | style="font-family:Segoe UI light; font-size:100%; solid #FFFFFF; background:#000000; text-align:center;" width="20.00%" | | ||
; | ; | ||
| − | [[AssignYL_Analysis| <font color="#FFFFFF"> | + | [[AssignYL_Analysis| <font color="#FFFFFF">NETWORK ANALYSIS</font>]] |
| style="font-family:Segoe UI light; font-size:100%; solid #FFFFFF; background:#000000; text-align:center;" width="20.00%" | | | style="font-family:Segoe UI light; font-size:100%; solid #FFFFFF; background:#000000; text-align:center;" width="20.00%" | | ||
| Line 75: | Line 75: | ||
<tr> | <tr> | ||
| + | </tr> | ||
| + | </table> | ||
| + | <br> | ||
| + | |||
| + | == Suspicious Records Exploration == | ||
| + | <br> | ||
| + | <table border='1'> | ||
| + | <tr> | ||
| + | <th>Findings</th> | ||
| + | <th>Visualization Evidence</th> | ||
| + | </tr> | ||
| + | <tr> | ||
<td><b> Suspicious Communications </b> | <td><b> Suspicious Communications </b> | ||
<br> | <br> | ||
| Line 81: | Line 93: | ||
</td> | </td> | ||
<td>[[File:YL Tblu 6.PNG|600px|center]][[File:YL Tblu 7.PNG|600px|center]]</td> | <td>[[File:YL Tblu 6.PNG|600px|center]][[File:YL Tblu 7.PNG|600px|center]]</td> | ||
| + | </tr> | ||
| + | <tr> | ||
| + | |||
| + | <td><b> Suspicious Network Overview </b> | ||
| + | <br> | ||
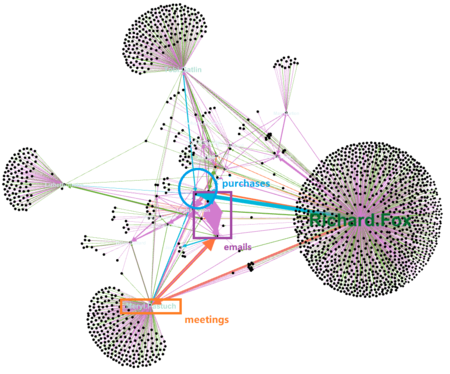
| + | The overview graph is plotted by everyone who is in the suspicious connection list whether it's the sender or receiver. For a directed graph, the person who was pointed by the arrow is the receiver. The number of connections is represented by thickness of the edge. | ||
| + | * '''Groups''': There are couple of isolated groups that are connected by a single person, yet most of the connections are one-time connection and no replies. People in the isolated groups of the graph may be copied or notified with an email that doesn't require any reply. | ||
| + | * '''Center of the Graph''': As we approach the center of the graph, more actual interactions have shown. Lots of suspicious emails have went around 2 person. Suspicious meetings are either pointed from or towars the same person - Meryl Pastuch. Most importantly, all suspicious purchases are pointed toward the same person. And all the nodes in the center are connected in a way. | ||
| + | </td> | ||
| + | <td>[[File:YL NW 1.PNG|450px|center]]</td> | ||
</tr> | </tr> | ||
<tr> | <tr> | ||
Latest revision as of 22:11, 10 July 2018
|
|
|
|
|
|
|
Company Overview
| Findings | Visualization Evidence |
|---|---|
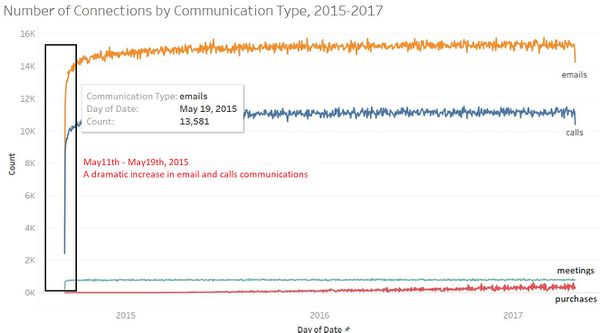
| Overall Patterns
|
|
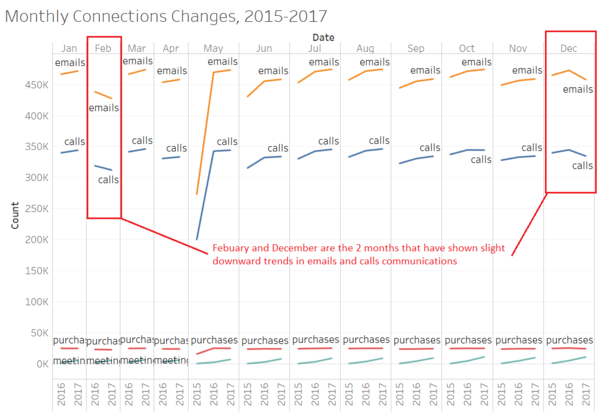
| Break down by Months
A more interesting question could be: what's causing the face-to-face shift since there is not much expansion in Kasios.
|
|
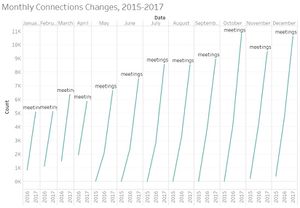
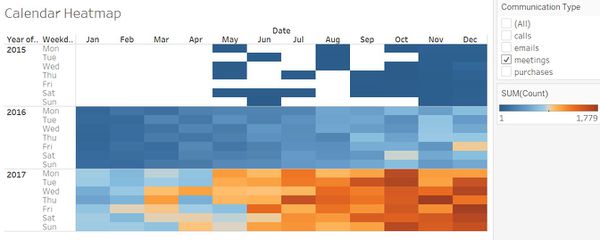
| Break down by Weeks
|
|
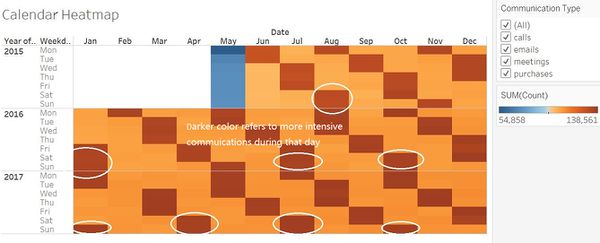
Suspicious Records Exploration
| Findings | Visualization Evidence |
|---|---|
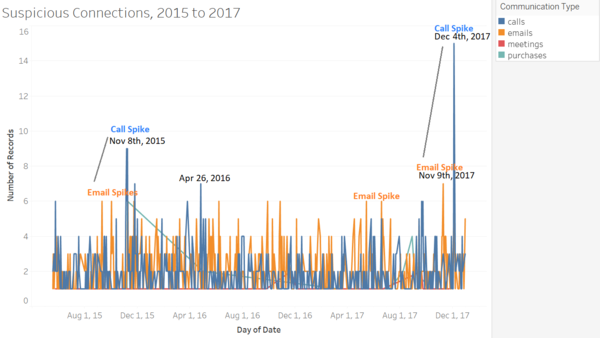
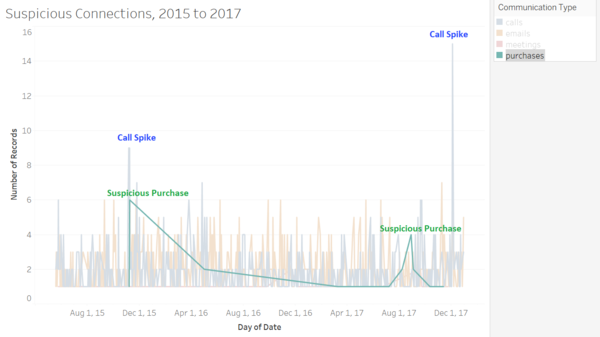
| Suspicious Communications
|
|
| Suspicious Network Overview
|
|