Difference between revisions of "ISSS608 2017-18 T3 Assign Aakanksha Kumari Q2"
Jump to navigation
Jump to search
| (6 intermediate revisions by the same user not shown) | |||
| Line 2: | Line 2: | ||
<div style="background:#DC143C; border:#DC143C; padding-left:15px; text-align:center;"> | <div style="background:#DC143C; border:#DC143C; padding-left:15px; text-align:center;"> | ||
| − | <font size = 5; color="#FFFFFF"><span style="font-family:Century Gothic;"> | + | <font size = 5; color="#FFFFFF"><span style="font-family:Century Gothic;">Unraveling the Secrets of Kasios : VAST Mini Challenge 3</span></font> |
</div> | </div> | ||
<!--MAIN HEADER --> | <!--MAIN HEADER --> | ||
| Line 29: | Line 29: | ||
; | ; | ||
[[ISSS608 2017-18 T3 Assign Aakanksha Kumari_Q4| <font color="#FFFFFF">Question 4</font>]] | [[ISSS608 2017-18 T3 Assign Aakanksha Kumari_Q4| <font color="#FFFFFF">Question 4</font>]] | ||
| − | |||
| − | |||
| − | |||
| − | |||
| style="font-family:Century Gothic; font-size:100%; solid #DC143C; background:#DC143C; text-align:center;" width="14.3%" | | | style="font-family:Century Gothic; font-size:100%; solid #DC143C; background:#DC143C; text-align:center;" width="14.3%" | | ||
| Line 46: | Line 42: | ||
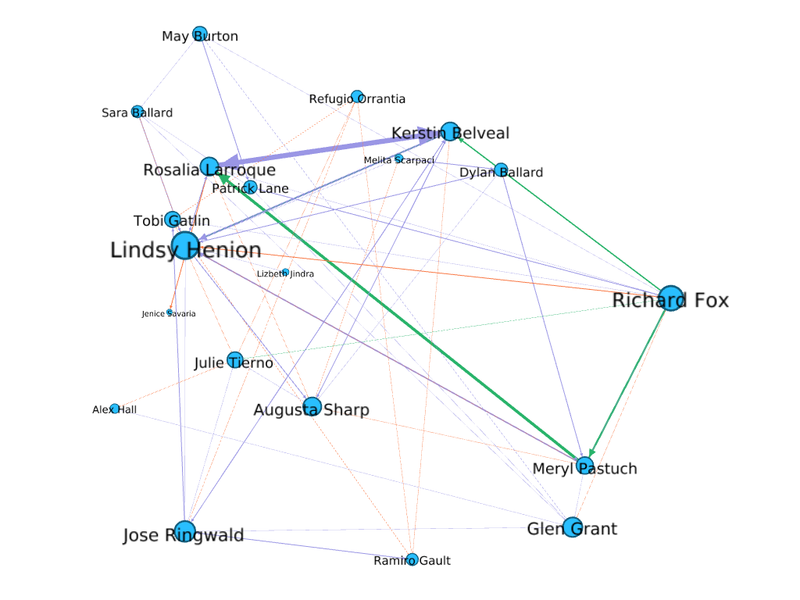
<big>'''''Combine the four data sources for group that the insider has identified as being suspicious and locate the group in the larger dataset. Determine if anyone else appears to be closely associated with this group. Highlight which employees are making suspicious purchases, according to the insider’s data.'''''</big> </div> | <big>'''''Combine the four data sources for group that the insider has identified as being suspicious and locate the group in the larger dataset. Determine if anyone else appears to be closely associated with this group. Highlight which employees are making suspicious purchases, according to the insider’s data.'''''</big> </div> | ||
|} | |} | ||
| + | |||
| + | === Suspicious Employees === | ||
| + | |||
| + | [[File:Only suspicious.png|800px|frameless|center]] | ||
| + | [[File:Legend.png|800px|frameless|center]] | ||
| + | |||
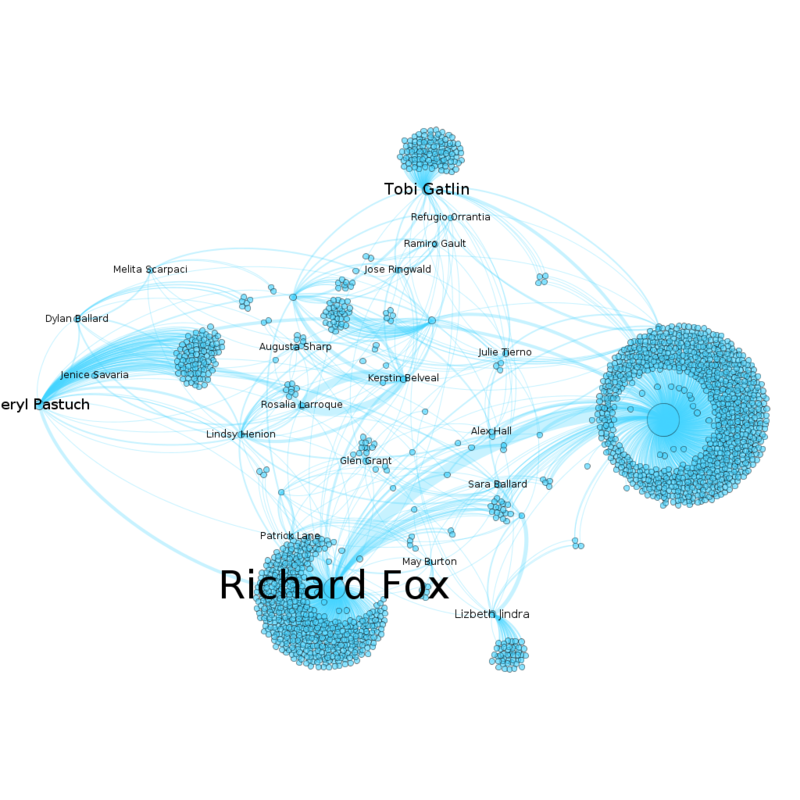
| + | === Suspicious Employess Organization Context === | ||
| + | |||
| + | [[File:All suspicious org.png|800px|frameless|center]] | ||
| + | |||
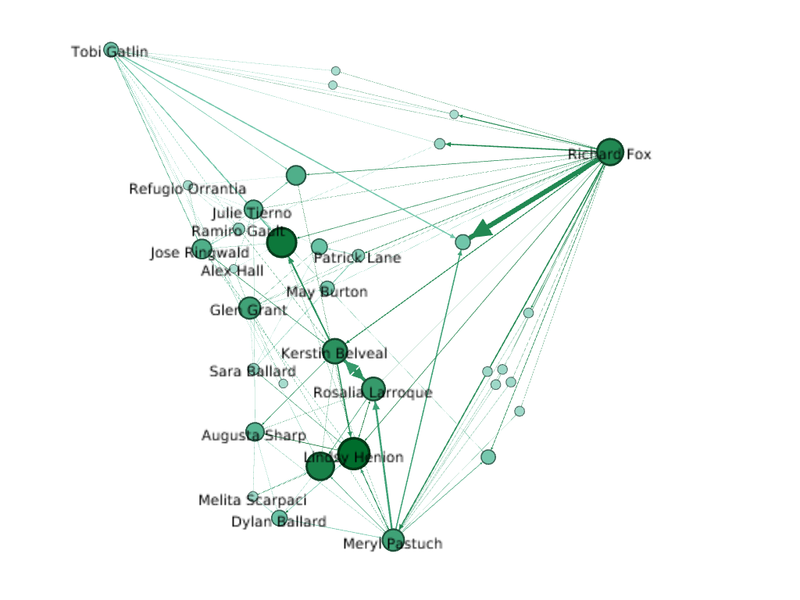
| + | === Other Closely Related Employees === | ||
| + | [[File:Other closely associated nodes.png|800px|frameless|center]] | ||
| + | [[File:legend_eigenvector.png|800px|frameless|center]] | ||
| + | |||
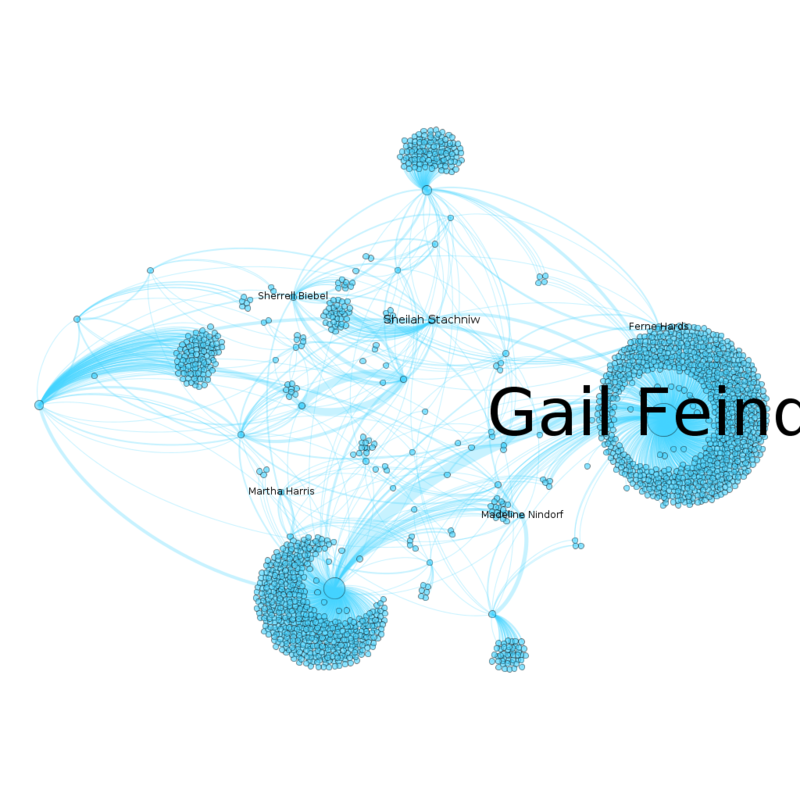
| + | === Other Closely Associated Nodes with Label === | ||
| + | [[File:Other closely associated nodes labels.png|800px|frameless|center]] | ||
| + | |||
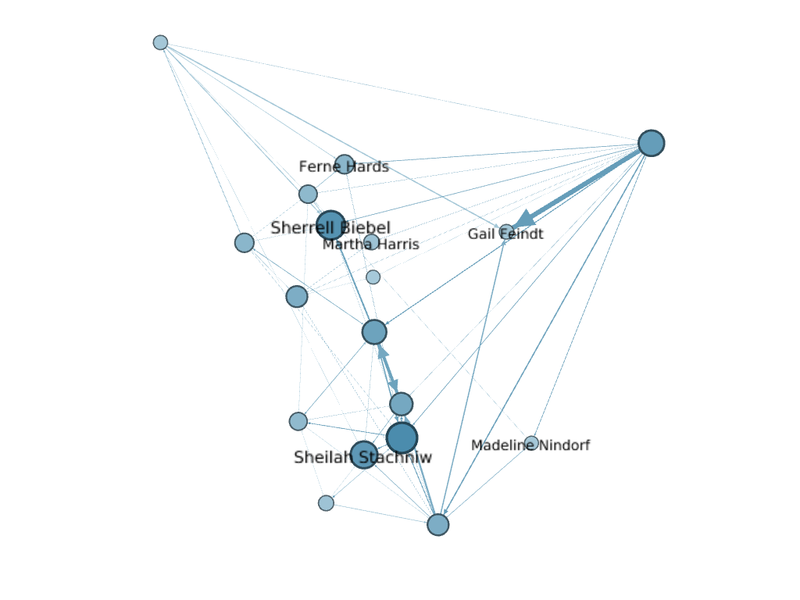
| + | === New Suspicious Employess Organization Context === | ||
| + | [[File:Other closely associated nodes org.png|800px|frameless|center]] | ||
Latest revision as of 13:11, 8 July 2018
Unraveling the Secrets of Kasios : VAST Mini Challenge 3
|
|
|
|
|
|
|
|
Combine the four data sources for group that the insider has identified as being suspicious and locate the group in the larger dataset. Determine if anyone else appears to be closely associated with this group. Highlight which employees are making suspicious purchases, according to the insider’s data.
|