ISSS608 2017-18 T3 Assign Vigneshwar Ramachandran Vadivel Q3
Using the combined group of suspected bad actors you created in question 2, show the interactions within the group over time. a. Characterize the group’s organizational structure and show a full picture of communications within the group. b. Does the group composition change during the course of their activities? c. How do the group’s interactions change over time? With the help of insider’s data about suspicious transactions, we can create a combined group of suspected bad actors to characterize the group.
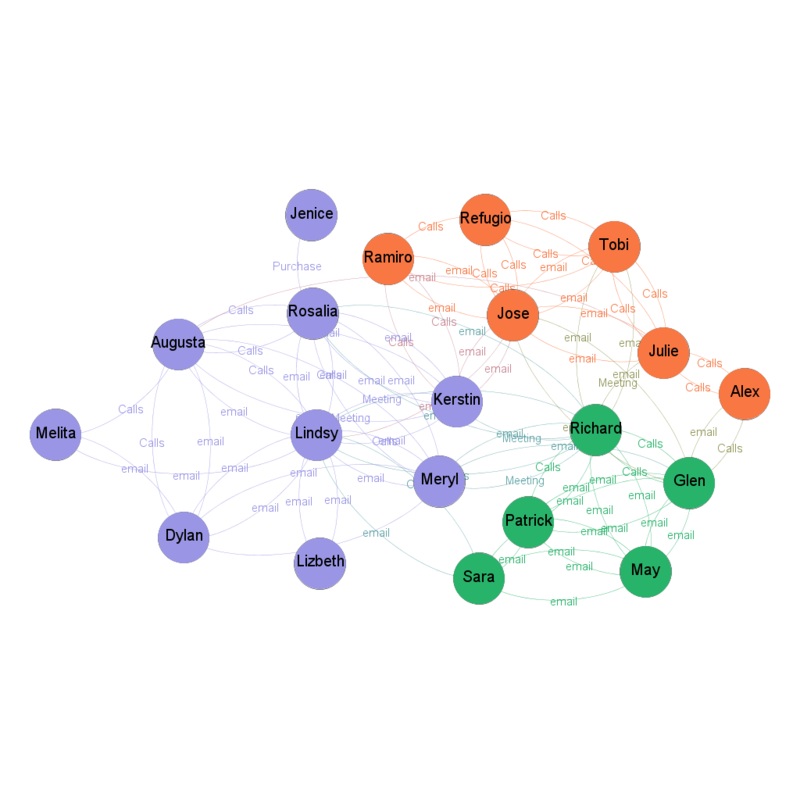
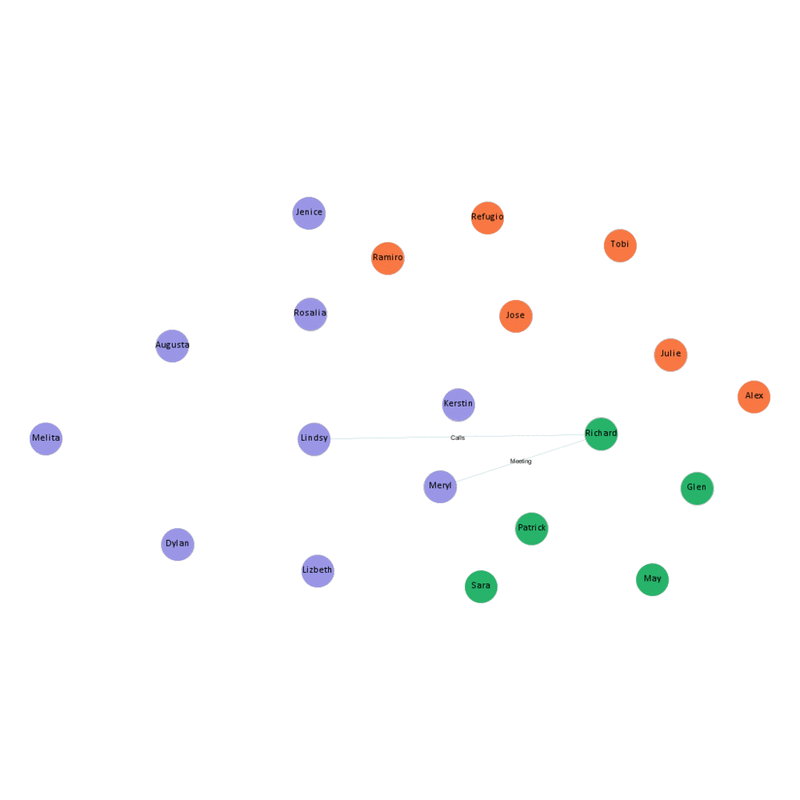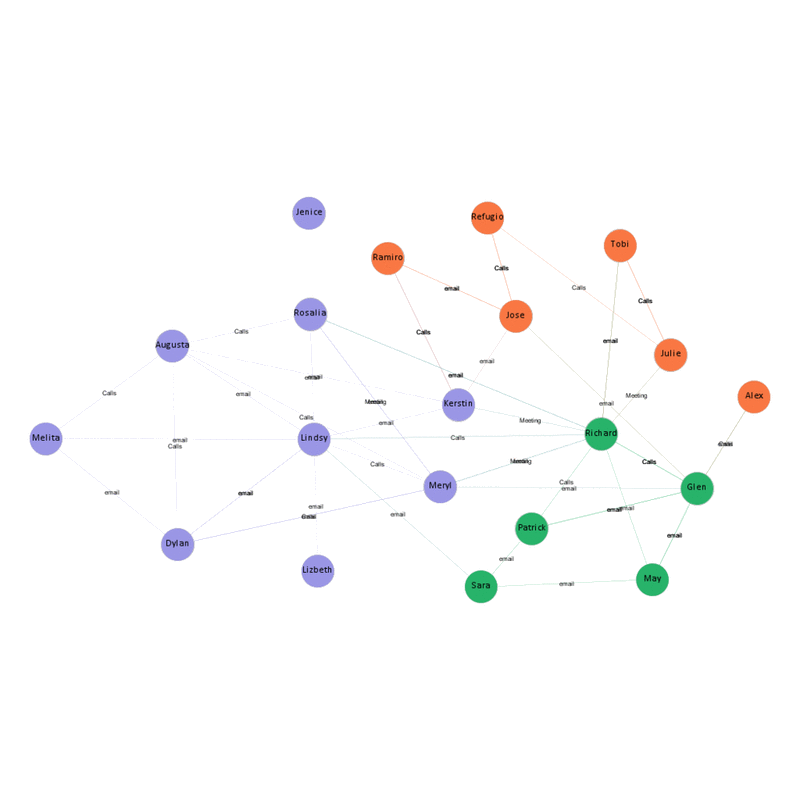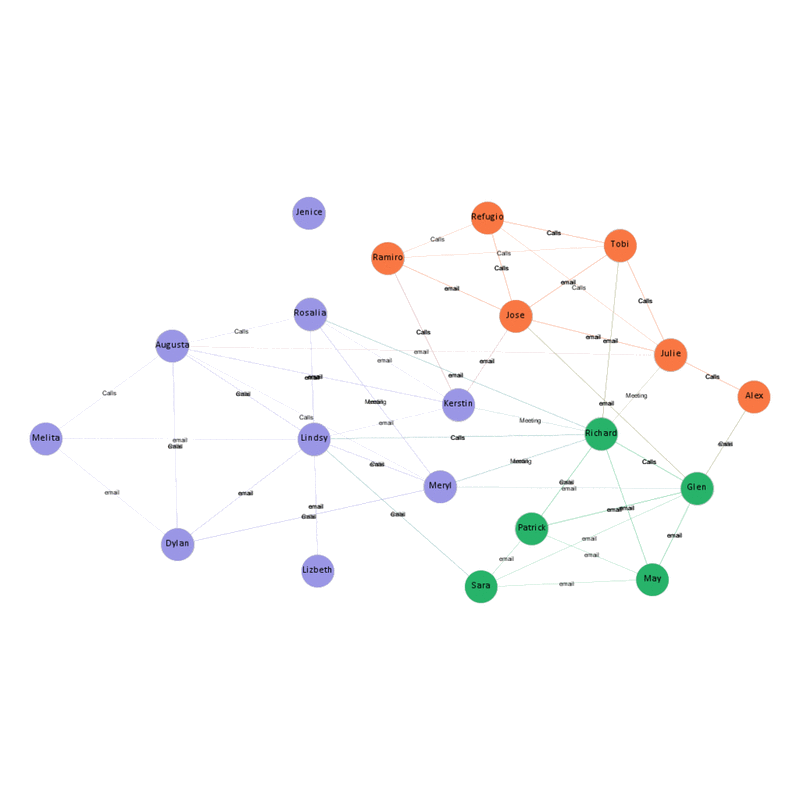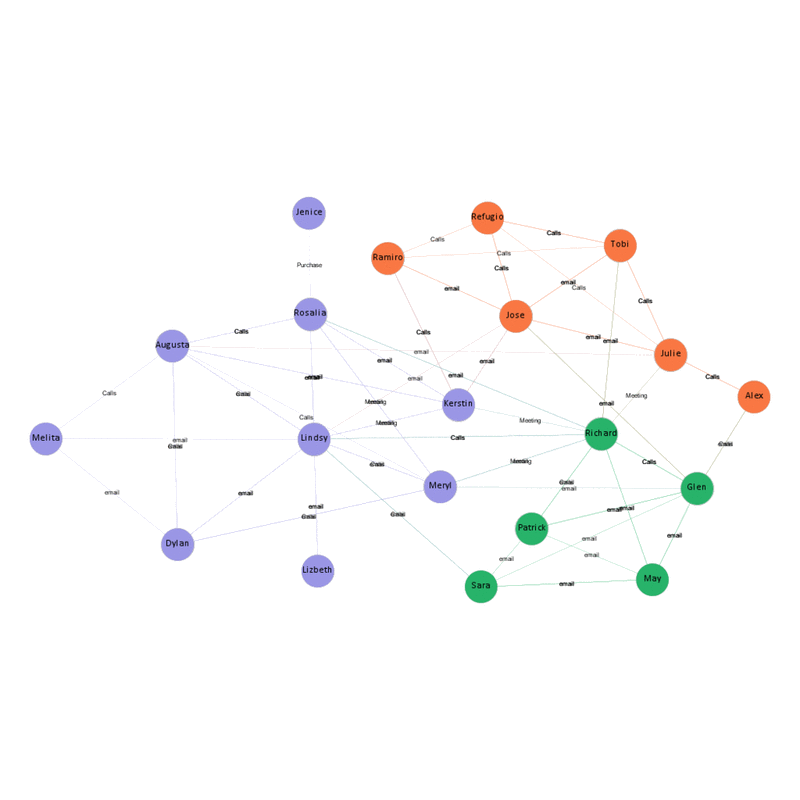
The below network shows the communication links among the suspected bas actors. As we can see the nodes represent the employee involved in the communication and the links shows the communication type.
To make the network more distinct, modularity algorithm can be implemented in Gephi which looks for the nodes that are more densely connected together than to the rest of the network. Now we can see three distinct clusters of employee within the suspicious network.
For finding very connected individuals or individuals who are likely to hold most information it’s useful to look at in-degree (number of inbound links) and out-degree (number of outbound links) as distinct measures.
Another measure which we are interested to look into is, Eigen Centrality to identify nodes with influence over the whole network, not just those directly connected to it.
Below interactive visualization allows us to explore the person of interest in the suspicious network and their internal link of communication.
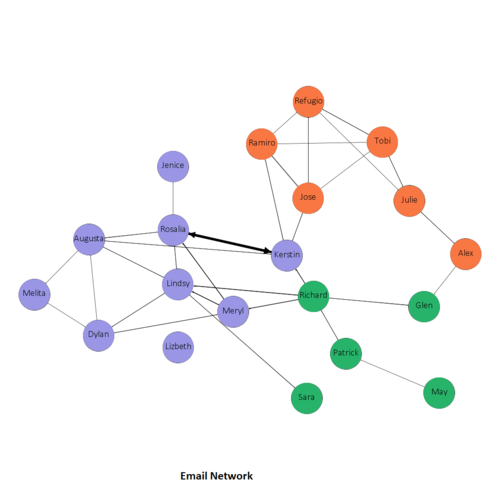
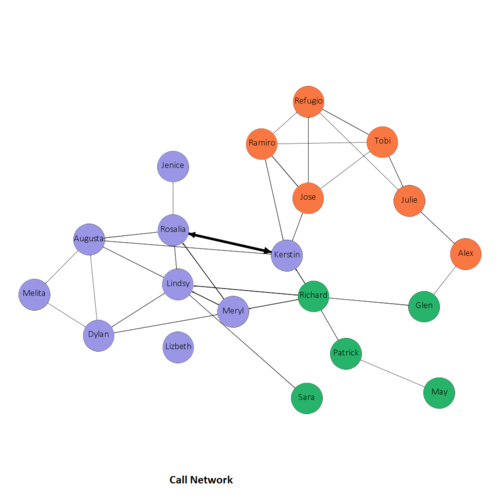
Using the filter in Gephi, we can narrow down to each communication type to understand whether the composition of the group changes with their activities,
Email network
Call Network
Purchase Network
Meeting Network
It is also important to identify whether the group’s interaction changes over time. To achieve this, we have to create timeline in gephi as decribed below,
Summary:
- Jenice and Lizabeth are only connected to the entire network through a single point of contact. This makes them vulnerable in the communication network since they are solely depending on other nodes for flow of information.
Hence even though the purchase is made by Jennice, her involvement in the illicit purchase is negligible. - Richard Fox, Tobi , Rosalia , Lindsy and Meryl influence the entire network and they are the main actors who are involved in the illicit purchase based on the graph metrics.