Difference between revisions of "ISSS608 2017-18 T3 Assign Hasanli Orkhan Insights"
Jump to navigation
Jump to search
Orkhanh.2017 (talk | contribs) |
Orkhanh.2017 (talk | contribs) |
||
| Line 38: | Line 38: | ||
<font size = 3; color="#FFFFFF"><span style="font-family:Century Gothic;">Who else appears to be closely associated with suspicious group?</span></font> | <font size = 3; color="#FFFFFF"><span style="font-family:Century Gothic;">Who else appears to be closely associated with suspicious group?</span></font> | ||
</div> | </div> | ||
| − | + | <br><br> | |
| + | <gallery mode="packed-hover" heights="300" > | ||
| + | File:Modul 0.png|Community_1 | ||
| + | File:Modul 1.png|Community_2 | ||
| + | File:Modul 2.png|Community_3 | ||
| + | File:Modul 3.png|Community_4 | ||
| + | File:Modul 4.png|Community_5 | ||
| + | File:Modul 5.png|Community_6 | ||
| + | </gallery> | ||
| + | <br><br> | ||
<br><br> | <br><br> | ||
| Line 59: | Line 68: | ||
<font size = 3; color="#FFFFFF"><span style="font-family:Century Gothic;">Group interactions over time</span></font> | <font size = 3; color="#FFFFFF"><span style="font-family:Century Gothic;">Group interactions over time</span></font> | ||
</div> | </div> | ||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
Revision as of 14:47, 8 July 2018
|
|
|
|
|
Changes over time in the company
Is the company growing?
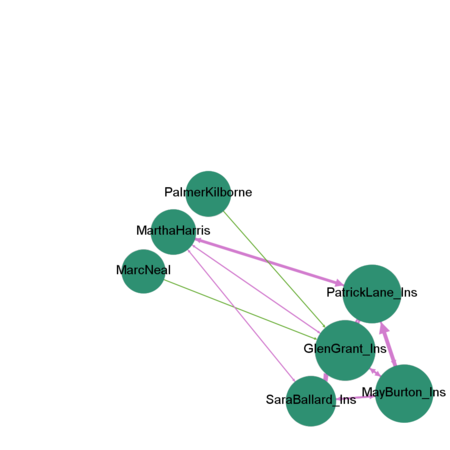
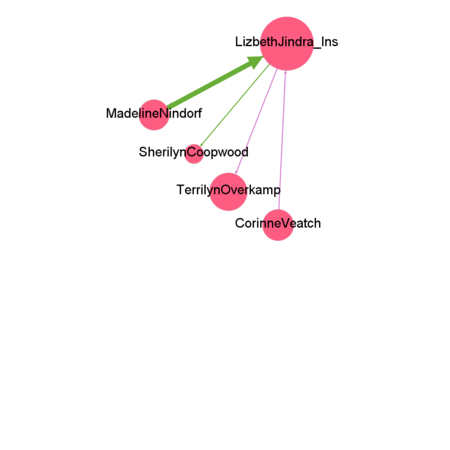
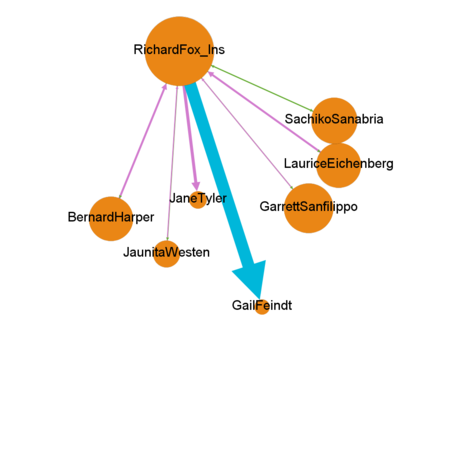
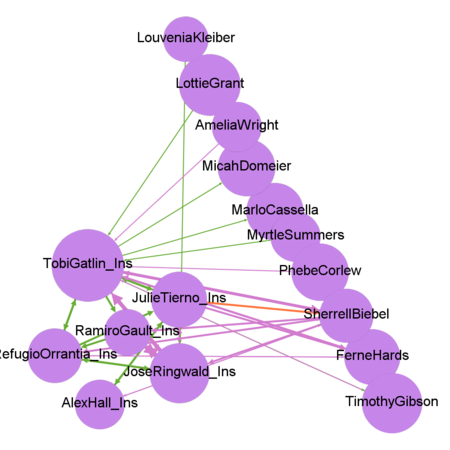
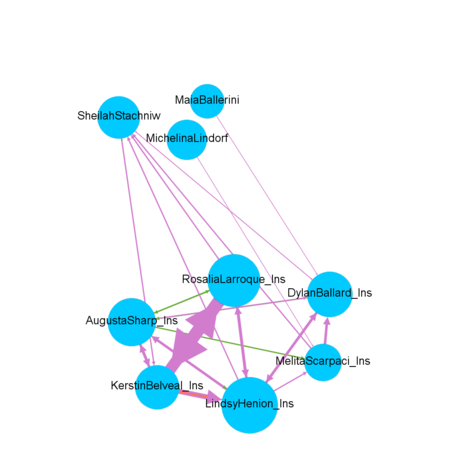
Who else appears to be closely associated with suspicious group?
Which employees are making suspicious purchases?
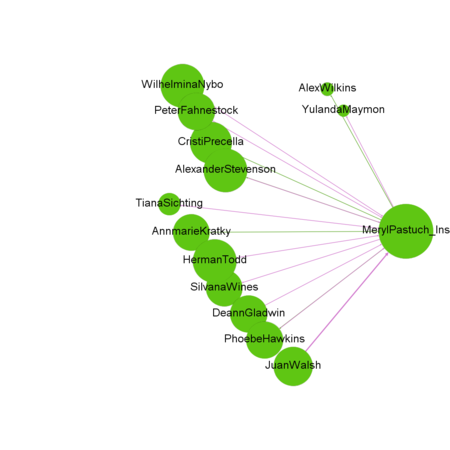
Organizational structure and a full picture of communications
Changes in the group composition depending on activities
Group interactions over time