Difference between revisions of "Group01 Proposal"
Vishalb.2017 (talk | contribs) (Created page with " <!--MAIN HEADER --> <div style="background:#3e4444; border:#124081; padding-left:15px; text-align:left;"> 500px|center <br> <font siz...") |
Yc.lim.2016 (talk | contribs) |
||
| (37 intermediate revisions by 4 users not shown) | |||
| Line 1: | Line 1: | ||
| + | LINK TO PROJECT GROUPS:<br /> | ||
| + | Please Click Here -> [https://wiki.smu.edu.sg/1718t3isss608/Project_Groups] | ||
<!--MAIN HEADER --> | <!--MAIN HEADER --> | ||
| − | <div style="background:# | + | [[File:1718T3_Group1_hacking.png|centre]] |
| − | + | <div style="background:#FFFFFF; border:#002060; padding-left:15px; text-align:center;"> | |
| − | + | <font size = 5; color="#000000"><span style="font-family:Century Gothic;">Cybersecurity | |
| − | <font size = 5; color="# | + | </span></font> |
| − | + | </div> | |
| − | |||
| − | |||
| − | </div> | ||
<!--MAIN MENU --> | <!--MAIN MENU --> | ||
| − | {|style="background-color:# | + | {|style=background-image:"linear-gradient(#fff, #ccc)"; background-color:"#222;" width="100%" cellspacing="0" cellpadding="0" valign="top" border="5" border-width="10" | |
| − | | style="font-family: | + | | style="font-family:'Droid Sans', sans-serif;; font-size:125%; solid:#1B338F; background:#222; text-align:center;" width="12%" | |
; | ; | ||
| − | |||
| − | | style="font-family: | + | [[Group01_Proposal|<font color="#FFFFFF">Proposal</font>]] |
| + | |||
| + | | style="font-family:'Droid Sans', sans-serif;; font-size:125%; solid #1B338F; background:#222; text-align:center;" width="12%" | | ||
; | ; | ||
| − | |||
| − | | style="font-family: | + | [[Group01_Poster| <font color="#FFFFFF">Poster</font>]] |
| + | |||
| + | | style="font-family:'Droid Sans', sans-serif;; font-size:125%; solid #1B338F; background:#222; text-align:center;" width="12%" | | ||
; | ; | ||
| − | |||
| − | + | [[Group01_Application| <font color="#FFFFFF">Application</font>]] | |
| − | |||
| − | [[Group01_Application| <font color="#FFFFFF"> | ||
| − | | style="font-family: | + | | style="font-family:'Droid Sans', sans-serif;; font-size:125%; solid #1B338F; background:#222; text-align:center;" width="12%" | |
; | ; | ||
| − | [[Group01_Report| <font color="#FFFFFF"> | + | |
| − | + | [[Group01_Report| <font color="#FFFFFF">Report</font>]] | |
|} | |} | ||
| Line 37: | Line 35: | ||
<!--OVERVIEW CONTENT --> | <!--OVERVIEW CONTENT --> | ||
==Abstract== | ==Abstract== | ||
| + | Data analytic has apparently become a hot topic in the workplace in recent years. While people are aspired to drive positive outcomes from data analytic, one generally overlooks at the dark side of the story – cyber security. | ||
| + | |||
| + | Cyber-attacks are becoming increasingly sophisticated. Coupled with the growing amount of data being generated by individuals, corporations and governments, well-orchestrated attacks could potentially cause major disruptions to any country, such as gaining access to national defense systems. In 28th Feb 2018, the media reported that the Ministry of Defence was hacked, resulting in the stolen data of 850 national servicemen and employee<sup>1</sup>. Regardless of the actual context, such news should really serve as alarm bells for extra efforts in the cyber security – one can not success in the Data world without a proper understanding of cyber security. | ||
| + | |||
| + | According to David Koh, CEO of Singapore’s Cyber Security Agency, Singaporeans are largely aware of cybersecurity threats but do not take the necessary precautions, which may be due to complacency stemming from Singapore's reputation as a safe country<sup>2</sup>. Hence, public education is still required to urge individuals into taking preventive measures. | ||
| + | |||
| + | This project will contribute to that end by providing interactive and interesting visulisations of cyber-attacks that can engage members of the public. As an extension of the project, the team may be able to provide a certain extent of prediction on where and how cyber attacks may happen. | ||
| + | |||
| + | <sup>1</sup>https://www.channelnewsasia.com/news/singapore/mindef-internet-system-breached-data-stolen-from-national-servic-7617146 | ||
| + | <sup>2</sup>https://govinsider.asia/innovation/cyber-war-csa-singapore-david-koh/ | ||
| + | |||
| + | ==Key Objectives== | ||
| + | '''1) Distribution of cyber attacks around the world'''<br /> | ||
| + | |||
| + | By creating a global map of the sources and targets of cyber attacks, users will be able to intuitively see the differences in intensity across regions at a certain point in time. <br /> | ||
| + | |||
| + | '''2) Evolution of cyber attacks around the world, over time'''<br /> | ||
| + | |||
| + | By creating an animated global map of the sources and targets of cyber attacks, using time-series data, users will be able to intuitively see the changes in intensity over time. <br /> | ||
| + | |||
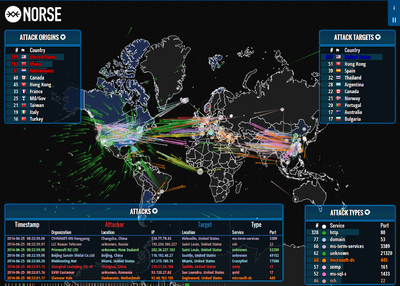
| + | Example:<br /> | ||
| + | [[File:Map of cyberattacks.png|400px]] | ||
==Project Timeline== | ==Project Timeline== | ||
| − | + | ||
| + | {| class="wikitable sortable" | ||
| + | |- | ||
| + | ! Task(s) !! Week | ||
| + | |- | ||
| + | | Confirmation of topic, data-set and proposal || 7 | ||
| + | |- | ||
| + | | Email consultation with Prof Kam for feedback on proposal || 8 (18 Jun) | ||
| + | |- | ||
| + | | Sketch out visual analytics solution || 9 | ||
| + | |- | ||
| + | | F2F consultation with Prof Kam for feedback on sketch || 10 | ||
| + | |- | ||
| + | | Implementation of visual analytics solution using Tableau/R|| 11 | ||
| + | |- | ||
| + | | F2F consultation with Prof Kam for feedback on progress/obstacles || 12 | ||
| + | |- | ||
| + | | Finalize the wiki report and poster || 13 | ||
| + | |- | ||
| + | | Poster presentation cum conference || 14 (14 Aug) | ||
| + | |} | ||
==Project Deliverable== | ==Project Deliverable== | ||
| Line 48: | Line 88: | ||
==Data Source== | ==Data Source== | ||
| − | + | AWS Honeypot Cyberattack dataset | |
| − | + | https://www.kaggle.com/casimian2000/aws-honeypot-attack-data/data | |
| + | |||
| + | The AWS Honeypot Database is an open-source database including information on cyber attacks/attempts. | ||
| + | Data has 451,581 data points collected from 9:53pm on 3 March 2013 to 5:55am on 8 September 2013. | ||
==Visualization Tools and Packages== | ==Visualization Tools and Packages== | ||
| − | Visualization using R | + | Visualization using a combination of Tableau and R. |
| − | |||
Latest revision as of 17:26, 12 August 2018
LINK TO PROJECT GROUPS:
Please Click Here -> [1]
Cybersecurity
|
|
|
|
|
Contents
Abstract
Data analytic has apparently become a hot topic in the workplace in recent years. While people are aspired to drive positive outcomes from data analytic, one generally overlooks at the dark side of the story – cyber security.
Cyber-attacks are becoming increasingly sophisticated. Coupled with the growing amount of data being generated by individuals, corporations and governments, well-orchestrated attacks could potentially cause major disruptions to any country, such as gaining access to national defense systems. In 28th Feb 2018, the media reported that the Ministry of Defence was hacked, resulting in the stolen data of 850 national servicemen and employee1. Regardless of the actual context, such news should really serve as alarm bells for extra efforts in the cyber security – one can not success in the Data world without a proper understanding of cyber security.
According to David Koh, CEO of Singapore’s Cyber Security Agency, Singaporeans are largely aware of cybersecurity threats but do not take the necessary precautions, which may be due to complacency stemming from Singapore's reputation as a safe country2. Hence, public education is still required to urge individuals into taking preventive measures.
This project will contribute to that end by providing interactive and interesting visulisations of cyber-attacks that can engage members of the public. As an extension of the project, the team may be able to provide a certain extent of prediction on where and how cyber attacks may happen.
1https://www.channelnewsasia.com/news/singapore/mindef-internet-system-breached-data-stolen-from-national-servic-7617146 2https://govinsider.asia/innovation/cyber-war-csa-singapore-david-koh/
Key Objectives
1) Distribution of cyber attacks around the world
By creating a global map of the sources and targets of cyber attacks, users will be able to intuitively see the differences in intensity across regions at a certain point in time.
2) Evolution of cyber attacks around the world, over time
By creating an animated global map of the sources and targets of cyber attacks, using time-series data, users will be able to intuitively see the changes in intensity over time.
Project Timeline
| Task(s) | Week |
|---|---|
| Confirmation of topic, data-set and proposal | 7 |
| Email consultation with Prof Kam for feedback on proposal | 8 (18 Jun) |
| Sketch out visual analytics solution | 9 |
| F2F consultation with Prof Kam for feedback on sketch | 10 |
| Implementation of visual analytics solution using Tableau/R | 11 |
| F2F consultation with Prof Kam for feedback on progress/obstacles | 12 |
| Finalize the wiki report and poster | 13 |
| Poster presentation cum conference | 14 (14 Aug) |
Project Deliverable
Data Source
AWS Honeypot Cyberattack dataset https://www.kaggle.com/casimian2000/aws-honeypot-attack-data/data
The AWS Honeypot Database is an open-source database including information on cyber attacks/attempts.
Data has 451,581 data points collected from 9:53pm on 3 March 2013 to 5:55am on 8 September 2013.
Visualization Tools and Packages
Visualization using a combination of Tableau and R.