Difference between revisions of "ISSS608 2017-18 T3 Assign Vigneshwar Ramachandran Vadivel Q4"
| (2 intermediate revisions by the same user not shown) | |||
| Line 38: | Line 38: | ||
<!------- End of Secondary Navigation Bar----> | <!------- End of Secondary Navigation Bar----> | ||
<div> Are there other groups that have structure and activity similar to this one? Who are they?<br> | <div> Are there other groups that have structure and activity similar to this one? Who are they?<br> | ||
| − | + | The insider has provided a list of purchases that might indicate illicit activity elsewhere in the company. Also we have the suspicious network of employee involved in the purchase of chemicals. | |
To identify the other suspicious activities it is important for us to understand the existing temporal structure of the suspicious purchase. | To identify the other suspicious activities it is important for us to understand the existing temporal structure of the suspicious purchase. | ||
| − | |||
</div> | </div> | ||
[[File:A1_MC3_Q4_Flow.gif|500px]] | [[File:A1_MC3_Q4_Flow.gif|500px]] | ||
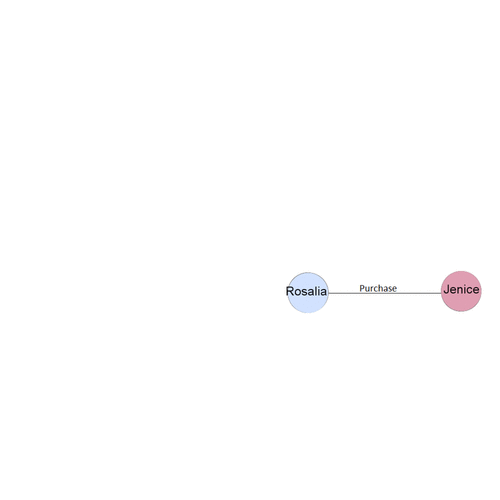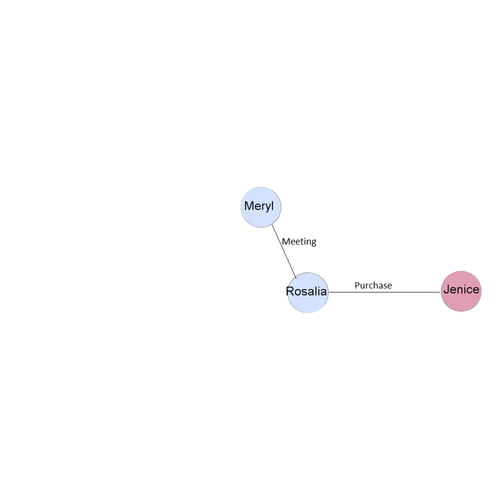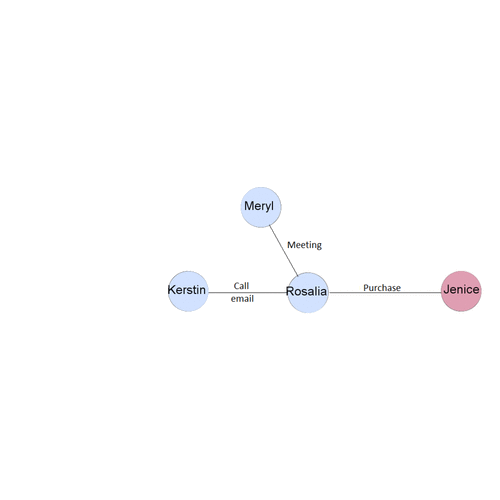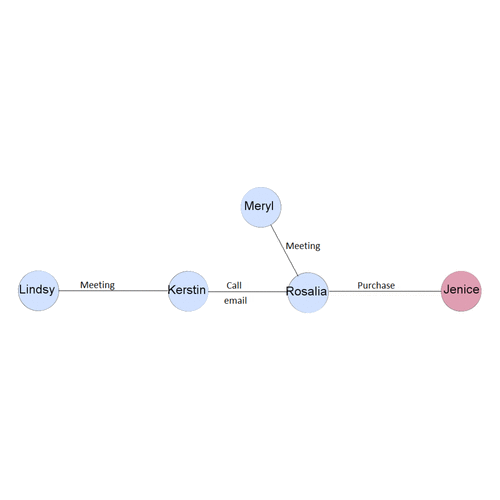
This visualization shows the flow of illicit purchase and its link with other employees. Now lets try to decode the other suspicious purchases to find the identical temporal patterns. | This visualization shows the flow of illicit purchase and its link with other employees. Now lets try to decode the other suspicious purchases to find the identical temporal patterns. | ||
| + | |||
| + | Based on the interactions with the suspicious network we can see the purchase intiated by <b>Carlos Morris</b> to <b>Laure Pelkey</b>on the 20th July 2017 day follows the same temporal pattern as the suspicious purchase spotted by the Kasios insider. | ||
Latest revision as of 13:27, 9 July 2018
The insider has provided a list of purchases that might indicate illicit activity elsewhere in the company. Also we have the suspicious network of employee involved in the purchase of chemicals. To identify the other suspicious activities it is important for us to understand the existing temporal structure of the suspicious purchase.
This visualization shows the flow of illicit purchase and its link with other employees. Now lets try to decode the other suspicious purchases to find the identical temporal patterns.
Based on the interactions with the suspicious network we can see the purchase intiated by Carlos Morris to Laure Pelkeyon the 20th July 2017 day follows the same temporal pattern as the suspicious purchase spotted by the Kasios insider.