Difference between revisions of "Staying Vigilant, Confronting Terrorism: Proposal"
Wx.tan.2013 (talk | contribs) |
Wx.tan.2013 (talk | contribs) |
||
| Line 112: | Line 112: | ||
<br/><div style="background: #364558; padding: 15px; font-weight: bold; line-height: 0.3em; text-indent: 15px;letter-spacing:-0.08em;font-size:20px"><font color=#fbfcfd face="Century Gothic">PROPOSED STORYBOARD</font></div> | <br/><div style="background: #364558; padding: 15px; font-weight: bold; line-height: 0.3em; text-indent: 15px;letter-spacing:-0.08em;font-size:20px"><font color=#fbfcfd face="Century Gothic">PROPOSED STORYBOARD</font></div> | ||
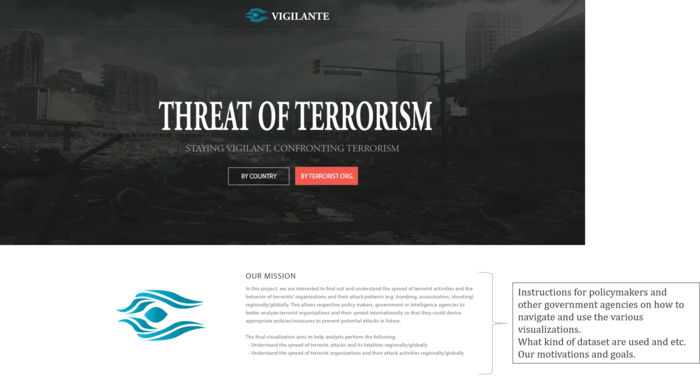
Our group has proposed the following storyboard to assist analysts in the use of our visual application: | Our group has proposed the following storyboard to assist analysts in the use of our visual application: | ||
| + | {| class="wikitable" style="background-color:#FFFFFF;" width="100%" | ||
| + | |- | ||
| + | ! style="font-weight: bold;background: #536a87;color:#fbfcfd;width: 50%;" | Proposed Layout | ||
| + | ! style="font-weight: bold;background: #536a87;color:#fbfcfd;" | How Analyst Can Conduct Analysis | ||
| + | |- | ||
| + | | | ||
| + | <p><center>'''Introduction''' </center></p> | ||
| + | [[File:Storyboard Intro (Page 1) Group7.png|700px|center]] | ||
| + | || | ||
| + | # Introduce analysts to the topic of terrorism and the objectives of the visualization project | ||
| + | # Select an option of whether they wish to analyze terrorist activities based on each country or each terrorist organization | ||
| + | |- | ||
| + | | | ||
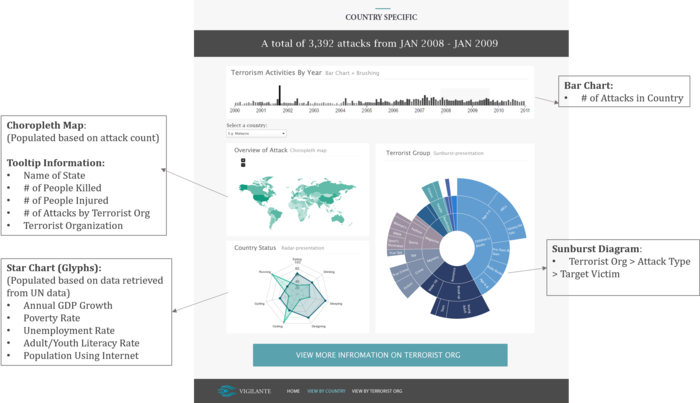
| + | <p><center>'''Analyze Terrorist Activities By Country''' </center></p> | ||
| + | [[File:Storyboard Country Specific (Page 2) Group7.png|700px|center]] | ||
| + | || | ||
| + | # Inspired by one of the related works mentioned previously, the filter in the page will be based on a bar chart showing the count of terrorist attacks over the years. | ||
| + | # A scrollbar will be implemented on the bar chart to allow users to choose the time series they are interested to look at. At any point in time, users can analyse one year of data. As the time period changes, the data in all 3 charts will change dynamically. | ||
| + | # A choropleth map of the country will be displayed and the count of terrorist attacks conducted in each state will be colored accordingly based on the selected time period. | ||
| + | # A star chart (glyph) will also be displayed to show the development state of the country for the selected time period. | ||
| + | # A zoomable sunburst diagram will also be displayed to show the terrorist organizations active in the country, the type of attacks conducted by each terrorist organization and their target types. | ||
| + | # By selecting to view more information about the terrorist organization, the user will be directed to the next page about the terrorist organizations. | ||
| + | |- | ||
| + | | | ||
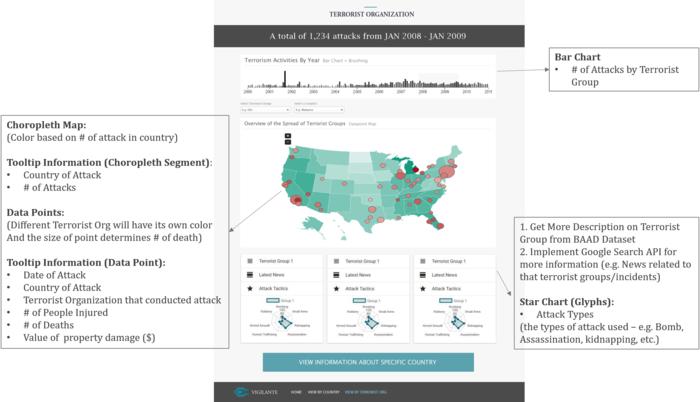
| + | <p><center>'''Analyze Terrorist Activities By Terrorist Organizations''' </center></p> | ||
| + | [[File:Storyboard Terrorist Org Specific (Page 3) Group7.png|700px|center]] | ||
| + | || | ||
| + | # If user enters the page from the country specific page, the top 3 active terrorist organization in the country will be shown. Otherwise, the top 3 active terrorist organization globally will be shown. | ||
| + | # Similar to the country specific page, a bar chart showing the count of attacks occurring globally will be shown. At any point in time, users can analyse one year of data. As the time period changes, the data in all charts will change dynamically. | ||
| + | # Other than the time period, users can also choose to add/remove the terrorist organizations they wish to compare against. If the country is selected as a filter, the top 3 terrorist organization in the country will be displayed. | ||
| + | # The choropleth world map will be colored based on the number of attacks conducted by the selected terrorist organizations. | ||
| + | # The data points on the choropleth world map will be colored by the different types of the terrorist organization who conducted the attack. The size of the data point will be determined by the number of deaths in the particular attack. | ||
| + | # More information about the terrorist organization will also be displayed. These information will come from the BAAD dataset, Google Search and the GTD dataset on the number of attacks conducted by its attack type. | ||
| + | |- | ||
| + | |} | ||
<br/><div style="background: #364558; padding: 15px; font-weight: bold; line-height: 0.3em; text-indent: 15px;letter-spacing:-0.08em;font-size:20px"><font color=#fbfcfd face="Century Gothic">ADDRESSING KEY TECHNICAL CHALLENGES</font></div> | <br/><div style="background: #364558; padding: 15px; font-weight: bold; line-height: 0.3em; text-indent: 15px;letter-spacing:-0.08em;font-size:20px"><font color=#fbfcfd face="Century Gothic">ADDRESSING KEY TECHNICAL CHALLENGES</font></div> | ||
Revision as of 23:22, 6 October 2016
The threat of terrorism is growing everyday and many countries, including Singapore, have taken steps to mitigate the risks of terrorism. In the National Day Rally 2016, PM Mr. Lee Hsien Loong mentioned that diplomats and security forces have been doing their job well but despite their efforts, it does not mean that terrorist attacks will not happen in Singapore. The recent attack that attempted to fire a rocket to hit Marina Bay Sands Area from Batam was successfully intervened but this signals to the country that the terrorism threat should not be taken lightly. In response to the growing terrorist threat, the SGSecure Movement was launched to prepare the public in the event of an attack. In recent years, there is a rise in research on terrorist organizations and the activities they have performed, regardless of scale, over the years. However, more still needs to be done to analyze past terrorist activities and gain insights from it easily so that all countries could better prepare for a worst case scenario.
In this project, we are interested to create a visualization that helps analysts perform the following:
- Identify terrorist organizations active in each country and the spread/types of activities they conducted to threaten the safety of the country, over different time periods
- Identify possible linkages between the number of terrorist activities occurring in a country and its development status
- Get a clearer understanding of each terrorist organization and the type of attacks they have conducted in a country/globally, over different time periods
- Compare different terrorist organizations and identify similarities and differences in their attack patterns, over different time periods
By conducting the analysis, it allows respective policy makers, government or intelligence agencies to better understand terrorist organizations and their spread internationally so that they could devise appropriate policies/measures to prevent potential attacks within their own country, regionally or globally in future.
The dataset for analysis will be retrieved from multiple databases, as elaborated below:
| Dataset/Source | Data Attributes | Rationale Of Usage |
|---|---|---|
(https://www.start.umd.edu/gtd/using-gtd/) |
|
|
(https://dataverse.harvard.edu/dataset.xhtml?persistentId=hdl%3A1902.1/16062) |
|
|
(Retrieved from World Bank) |
|
between the number of terrorist activities occurring in the country and its development state. |
(Retrieved from UN Data - UNESCO Institute for Statistics) |
|
between the number of terrorist activities occurring in the country and its development state. |
(Retrieved from UN Data - International Telecommunications Union) |
|
between the number of terrorist activities occurring in the country and its development state. |
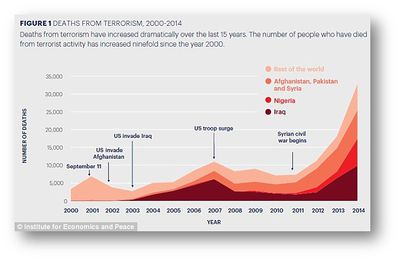
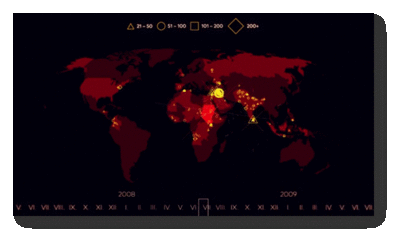
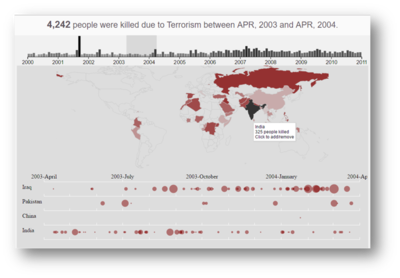
Many visual and data analysts have made use of data collected from the Global Terrorism Database to visualize and understand the extent of terrorist attacks around the world. Some of their works include the following:
| Related Works | What We Can Learn |
|---|---|
|
|
|
| |
|
Our group has proposed the following storyboard to assist analysts in the use of our visual application:
| Proposed Layout | How Analyst Can Conduct Analysis |
|---|---|
|
|
|
|
|
|
|
|
|
The following are some of the key technical challenges that we may face throughout the course of the project:
| Key Technical Challenges | How We Propose To Resolve |
|---|---|
| |
| |
| |
|
The following shows our project timeline for the completion of this project:
Feel free to comment to help us improve our project! (: